Time-consuming, paper-based Know Your Customer (KYC) procedures have become a simple, digital-first process called electronic Know Your Customer (eKYC). eKYC technology enables companies to remotely authenticate customers, enhancing security, efficiency, and customer satisfaction.
eKYC makes use of state-of-the-art technologies like artificial intelligence (AI), biometrics, and optical character recognition (OCR) for authenticating an individual in real-time. We will discuss here how eKYC verification process works, what are the challenges involved, and how it helps businesses and customers.
What is eKYC Verification?
eKYC (Electronic Know Your Customer) verification is a digital method of verifying a person’s identity electronically, thereby avoiding the normal paper process. eKYC verification is regularly used by many banks, financial institutions, and other service providers to safely and effectively identify customers.
Key Differences Between Traditional KYC and eKYC
| Feature | Traditional KYC | eKYC (Electronic KYC) |
| Verification Mode | Physical verification (in-person) | Online verification (via biometrics, OTP, or AI-based checks) |
| Documents Needed | Physical copies of ID, address proof, etc. | Digital copies or Aadhaar-based authentication |
| Security | Prone to document loss, forgery, and human errors | More secure with encryption, biometric, and AI-based verification |
| Regulatory Compliance | Follows traditional banking/KYC norms | Compliant with digital verification standards like Aadhaar eKYC (India), eID (EU) |
| Adoption | Used in conventional banks and financial institutions | Widely used in fintech, digital banking, and online services |
Benefits of eKYC
- Enhanced Security: Eliminates the danger of identity theft via biometric verification, encryption, and real-time authentication.
- Improved Onboarding Effectiveness: Automates customer verification processes, eliminating paper and reducing human error.
- Regulatory Compliance: Seeks regulatory compliance with finance laws and regulations by ensuring proper and secure documentation of identities.
How Does the eKYC Process Operate?
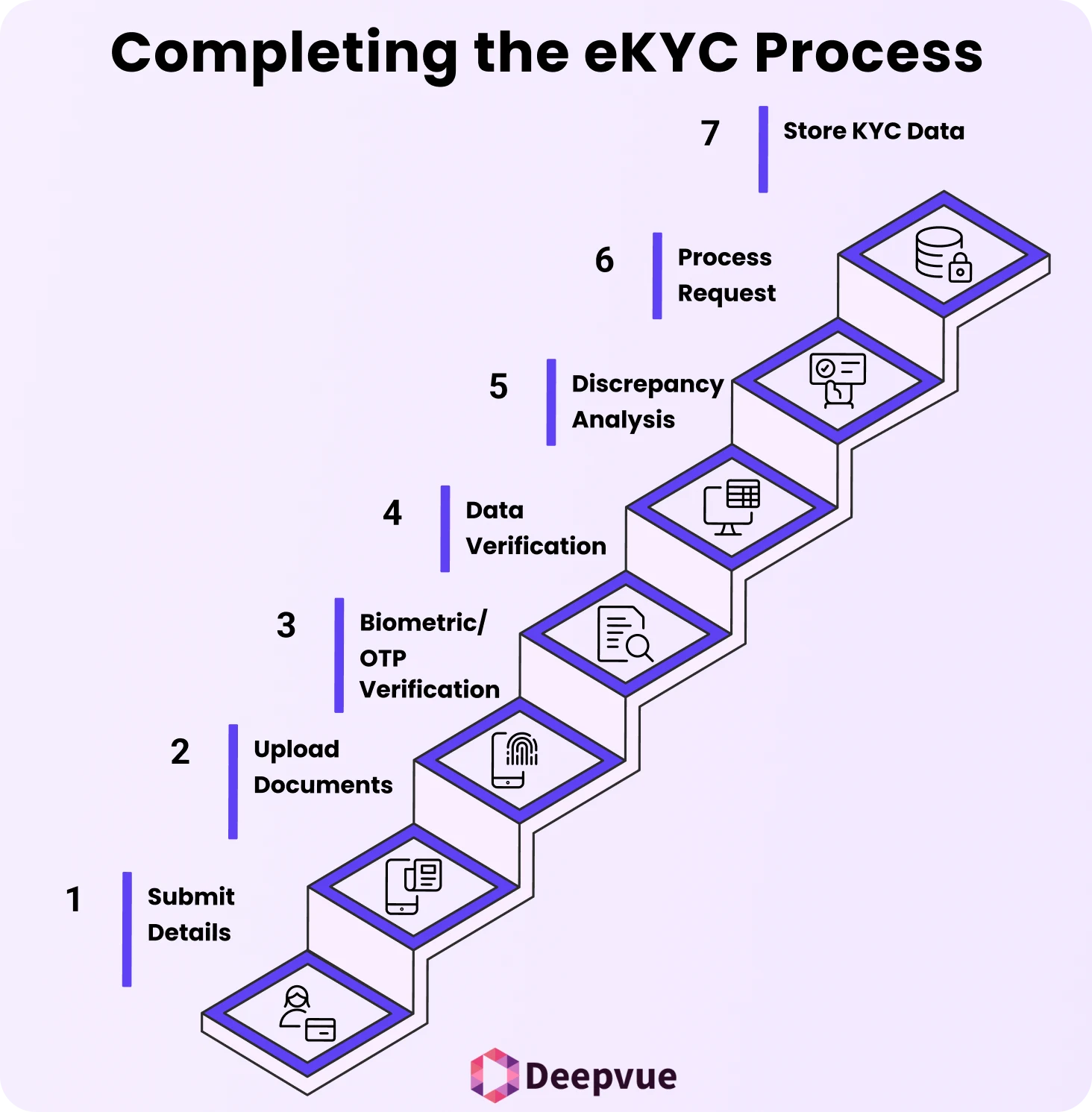
- The customer starts the eKYC (Electronic Know Your Customer) process by submitting their details through a digital platform.
- The customer uploads images or scans of identity and address proof (e.g., driving license, Aadhaar, passport).
- The system verifies identity by biometric authentication (fingerprint, face scan) or a one-time password (OTP) sent to a registered mobile number.
- The data presented is verified against government records or other sources of provenance for correctness.
- Machine learning and artificial intelligence software can analyze patterns to identify discrepancies or deceit.
- Once found to be equivalent, the request for eKYC is processed. If any discrepancies are identified, further verification or rejection occurs.
- Upon confirmation, customer KYC data is safely stored for future use to ensure compliance.
Technologies Used in eKYC
- Artificial Intelligence (AI) & Machine Learning (ML): Automates identity verifications, fraud, and risk assessments.
- Optical Character Recognition (OCR): Reads and imports text from identification documents such as passports and driver’s licenses.
- Biometric Authentication: Facilitates access using facial identification, fingerprint reads, and eye scans to establish identity.
- Liveness Detection: Ensures the user is physically present through the detection of live facial responses and movement.
- Application Programming Interfaces (APIs): Bridges eKYC systems to banks, fintech players, and government databases.
How is eKYC Verification through Aadhaar Done?
- The user consents to Aadhaar-based eKYC authentication.
- The authentication will either be done through OTP (One-Time Password) or biometric authentication (iris scan/fingerprint).
- The user inputs his Aadhaar number on the portal of the service provider, receives an OTP sent to the registered mobile number, and inputs it as verification.
- The person then goes to the premises of a service provider, where they compare their iris scan or fingerprint with UIDAI records.
- On successful authentication, UIDAI provides the authenticated information such as name, address, date of birth, and photo to the requesting agency.
- No paper records are required since information is computer-verifiable and secure storage.
- The process is secured and is by UIDAI standards for data security and legal compliance
Challenges and Limitations of eKYC
- Security Risks: eKYC implies the processing of sensitive financial and personal information and, therefore, is an open target for online attacks and identity theft. Data breaches and identity theft may lead to unauthorized access to and use of personal data.
- Accessibility Problems: Lack of proper internet connectivity and poor digital literacy could keep users, particularly rural or developing area users, from reaching eKYC services. Users might lack the required technology, i.e., smartphones or biometric readers, to undergo the verification process.
- Regulatory Barriers: Differing regulatory and compliance requirements in countries create a challenge in eKYC standardization worldwide. Strict data protection laws such as GDPR impose restrictions on the collection, storage, and transmission of personal data.
Importance of Digital Identity Verification
- Effect on Anti-Fraud: Digital identity verification assists companies and financial institutions in identifying and preventing fraud. It ensures that genuine users can use services, minimizing the risk of duplicate accounts and unauthorized transactions.
- Identity Theft Protection: Digital identity verification provides an additional layer of protection, and it is challenging for cyber thieves to utilize stolen identity information. It deters unauthorized utilization of financial accounts, government agencies, and personal information.
Implementing eKYC Solutions
- Business Needs Assessment: Identify the specific customer identity verification needs and issues. Document the security, automation, and integration needs.
- Selecting the Right Technology Partner: Evaluate potential vendors based on their experience, technology, and compliance levels. Check for AI and biometric verification features to improve security.
- Ensuring Regulatory Compliance: Comply with local and global KYC/AML laws (e.g., GDPR, FATF, RBI, FINCEN). Practice secure data management, encryption, and storage. Periodically audit eKYC processes to ensure regulatory compliance.
- eKYC Process Monitoring and Upgradation: Ongoing monitoring of the performance of the eKYC system and end-user feedback. Security controls updation to tackle new fraud methods.
Conclusion
eKYC verification is transforming the way businesses authenticate customer identities, making the process faster, more secure, and highly efficient. From fintech and banking to healthcare and e-commerce, sectors are adopting digital identity verification to ease onboarding, improve customer experience, and protect sensitive data. Companies need to have robust security in place and remain compliant with changing regulatory requirements to reap the full advantages of eKYC.
To learn how Deepvue’s Verification Suite can streamline your Aadhaar eKYC process, go to Deepvue.tech and check out their cutting-edge APIs that are made for precision and speed
FAQs
How does eKYC verification work?
The biggest difference is that eKYC is purely electronic and sometimes even automated (using biometrics or AI), whereas digital KYC can have manual steps too, like customers submitting scanned images of physical documents to be examined.
Which industries use eKYC?
Those that make extensive use of eKYC are banking and FinTech (for opening accounts and loans), telecom (for activation of SIM cards), healthcare (for onboarding patients), and cryptocurrency and gaming sites (for verification of age and identity).
Can eKYC avert identity fraud?
Yes, eKYC prevents identity fraud through the application of AI to identify artificial or tampered documents, ensuring that the user is physically present using liveness checks, and comparing identity information with trusted databases to raise alarm for suspicious behavior.
How does eKYC differ from digital KYC?
The biggest difference is that eKYC is purely electronic and sometimes even automated (using biometrics or AI), whereas digital KYC can have manual steps too, like customers submitting scanned images of physical documents to be examined.
Can eKYC avert identity fraud?
Yes, eKYC prevents identity fraud through the application of AI to identify artificial or tampered documents, ensuring that the user is physically present using liveness checks, and comparing identity information with trusted databases to raise alarm for suspicious behavior.