In today’s digital age, ensuring the security of our personal information is more crucial than ever. Traditional methods of authentication, such as passwords and PINs, are day-by-day becoming inadequate due to their vulnerability to breaches and misuse.
Enter face authentication, a sophisticated technology that leverages the uniqueness of an individual’s facial features to provide a secure and seamless authentication process. At Deepvue, we are at the forefront of providing advanced API infrastructure for financial integrations and insights, and face authentication is a key component of our security solutions.
What is Face Authentication?
Face authentication, also known as facial recognition or biometric authentication, is a method of identifying or verifying the identity of an individual by analyzing their facial features. This technology uses advanced algorithms and artificial intelligence to compare a person’s facial data with stored data to grant or deny access.
Unlike passwords or PINs, which can be easily forgotten or stolen, face authentication relies on unique biological features that are hard to replicate. This makes it a highly secure and user-friendly option for identity verification.
What is Liveness Detection in Face Authentication?
Liveness detection in face authentication is a security feature that ensures the person trying to access a system is physically present and not using a photo, video, or mask. It uses techniques like blinking, facial movements, or 3D depth analysis to distinguish real faces from fake ones. This prevents spoofing attacks and enhances the reliability of biometric authentication, making identity verification more secure and trustworthy.
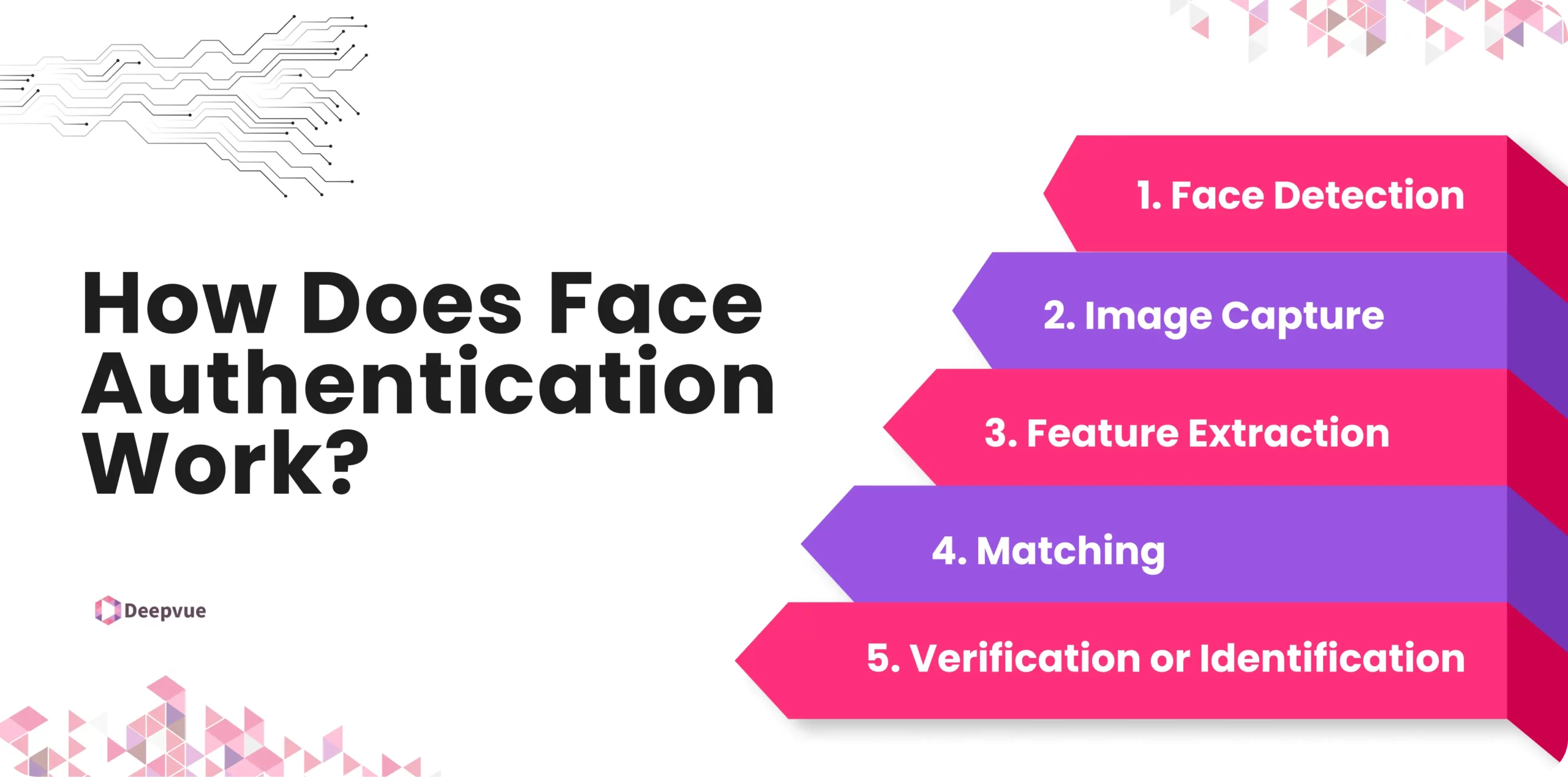
How Does Face Authentication Work?
Here’s how face authentication work-
1. Face Detection
The first step in face authentication is detecting the face in an image or video. This is typically done using a camera on a smartphone, tablet, or computer. The system scans the input to locate the face, distinguishing it from other objects in the frame.
2. Image Capture
Once the face is detected, the system captures an image or series of images. These images are usually taken from different angles and under various lighting conditions to create a comprehensive dataset of the person’s face.
3. Feature Extraction
The next step involves extracting unique facial features from the captured images. This can include the distance between the eyes, the shape of the nose, the contour of the lips, and the structure of the cheekbones. Advanced algorithms analyze these features to create a digital representation, often referred to as a faceprint.
4. Matching
The faceprint is then compared to a database of stored faceprints. This database could belong to a device’s user, an organization’s employee records, or a government database like Aadhaar. The system checks for a match by analyzing similarities and differences between the faceprint and the stored faceprints.
5. Verification or Identification
If a match is found, the system proceeds to verify or identify the individual. Verification confirms the identity of the person, while identification determines who the person is from a list of potential matches. This step often includes additional security checks to prevent spoofing or fraud.
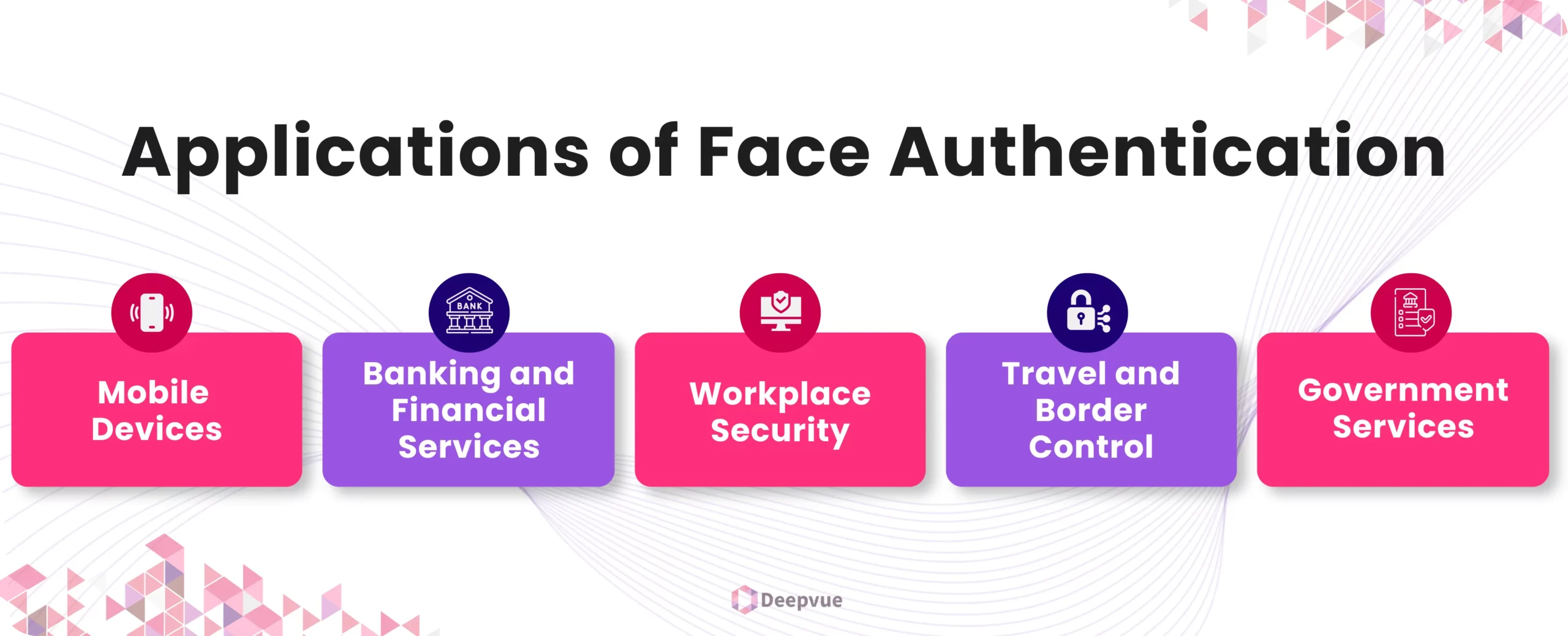
Applications of Face Authentication
Face authentication has a wide range of applications across various industries. Here are a few common examples:
1. Mobile Devices
One of the most common uses of face authentication is in smartphones and tablets. Users can unlock their devices, access apps, and authorize payments simply by looking at their screens. This adds an extra layer of security beyond traditional passwords.
2. Banking and Financial Services
In the financial sector, face authentication is used for secure transactions and account access. Customers can verify their identity for online banking, mobile payments, and ATM withdrawals without needing physical cards or PINs.
3. Workplace Security
Organizations are adopting face authentication for employee access control. Employees can enter secure areas, log into systems, and clock in and out of work using facial recognition, reducing the risk of unauthorized access.
4. Travel and Border Control
Airports and border control agencies use face authentication to streamline security checks and enhance traveler experiences. Passengers can pass through automated gates using their faces, speeding up the boarding process and reducing wait times.
5. Government Services
Governments around the world are leveraging face authentication for various services. In India, face authentication is integrated into the Aadhaar system to provide citizens with secure access to government benefits and services.
What is Face Authentication in Aadhaar?
Aadhaar, the world’s largest biometric ID system, is a unique identification number issued to Indian residents. It uses biometric data, including fingerprints and iris scans, to authenticate identities. Recently, face authentication has been added as an additional layer of security.
How It Works in Aadhaar
When a person enrolls for Aadhaar, their facial image is captured along with other biometric data. This facial image is then converted into a faceprint and stored in the Aadhaar database. During authentication, the captured faceprint is compared to the stored one to verify the person’s identity.
Benefits of Face Authentication in Aadhaar
- Enhanced Security: Face authentication adds an extra layer of security, making it difficult for fraudsters to impersonate someone else.
- Convenience: Users can authenticate themselves quickly and easily without the need for physical documents or remembering passwords.
- Inclusivity: Face authentication helps include individuals who may have difficulties with fingerprint or iris scans due to age, injury, or other reasons.
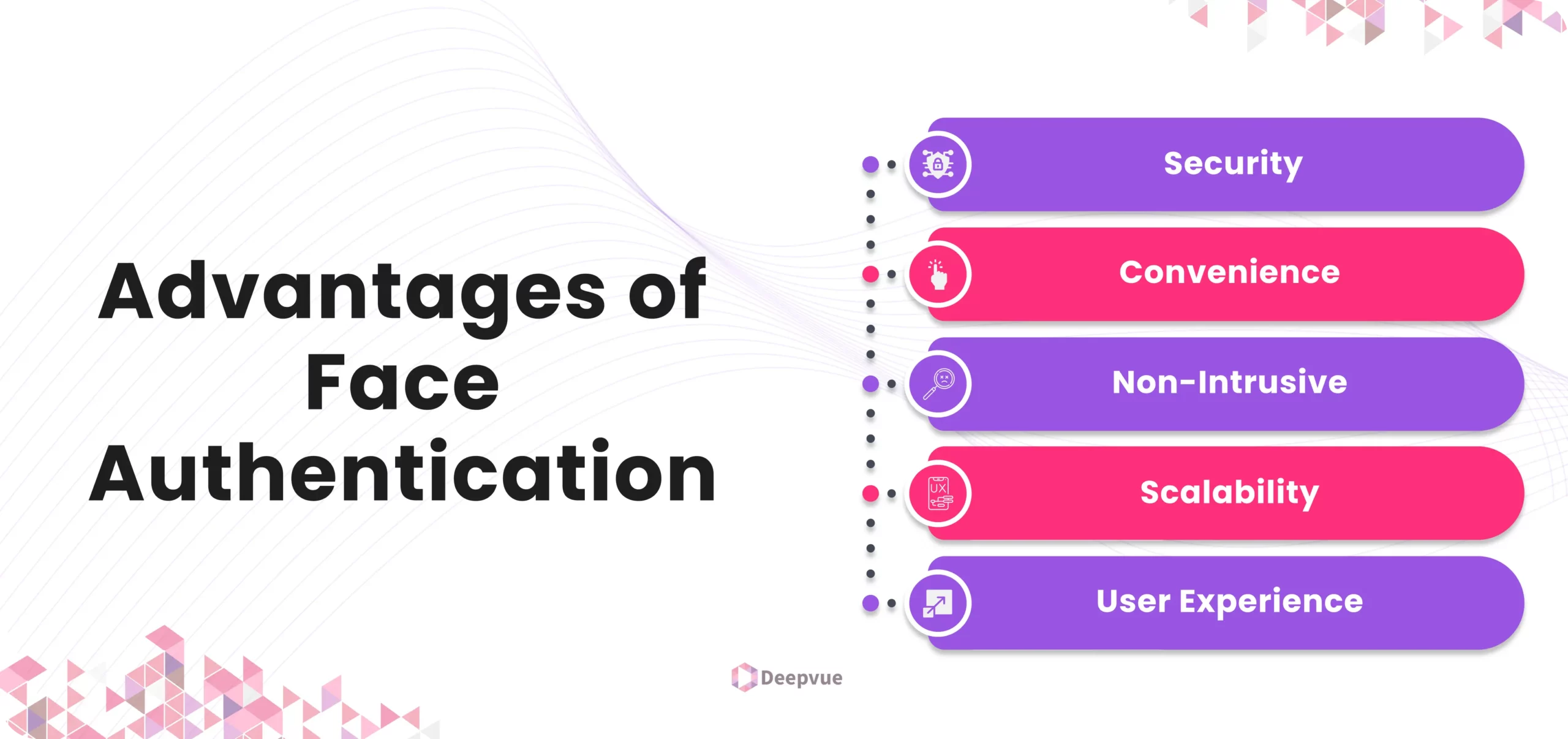
Advantages of Face Authentication
Face authentication offers numerous advantages over traditional authentication methods. Here are some key benefits:
1. Security
Facial features are unique to each individual, making face authentication highly secure. It is difficult for someone to replicate or steal another person’s faceprint.
2. Convenience
Face authentication is quick and easy to use. Users can authenticate themselves by simply looking at a camera, eliminating the need to remember passwords or carry physical tokens.
3. Non-Intrusive
Unlike some biometric methods, face authentication is non-intrusive. Users do not need to touch any device, which is particularly beneficial in hygiene-sensitive environments.
4. Scalability
Face authentication systems can be easily scaled to accommodate large numbers of users, making them suitable for organizations, governments, and large-scale applications.
5. User Experience
By providing a seamless and frictionless authentication process, face authentication enhances the overall user experience. This is especially important in customer-facing applications where ease of use is a priority.
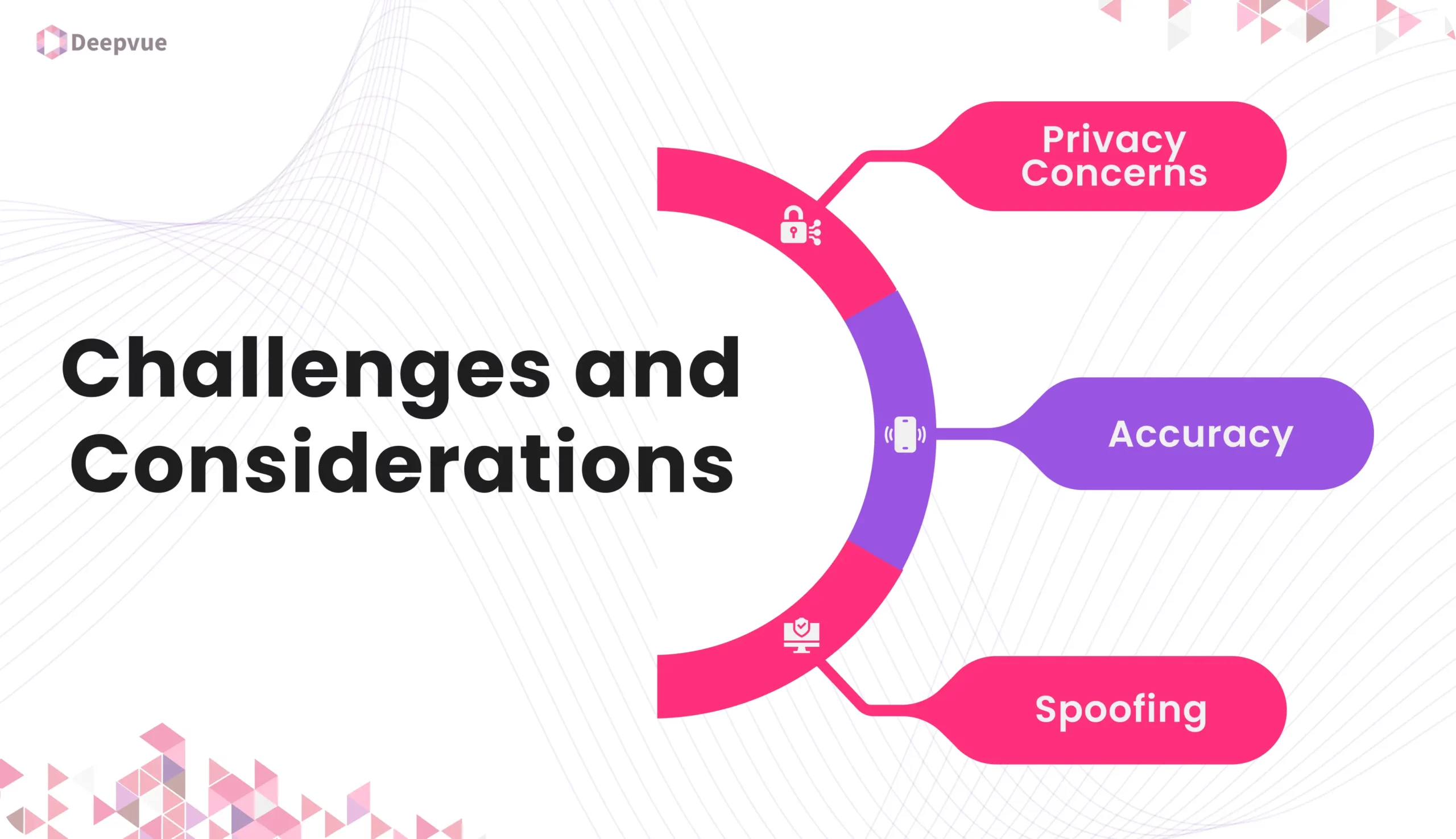
Challenges and Considerations
While face authentication offers many benefits, it is not without its challenges. Here are a few challenges:
1. Privacy Concerns
The use of biometric data raises privacy concerns. It is important to ensure that face authentication systems comply with data protection regulations and that users’ data is handled securely.
2. Accuracy
Factors such as lighting conditions, facial expressions, and changes in appearance can affect the accuracy of face authentication. Systems must be robust enough to handle these variations.
3. Spoofing
Face authentication systems must be equipped with anti-spoofing measures to prevent fraudsters from using photos, videos, or masks to trick the system.
The Future of Face Authentication
Face authentication is a powerful and evolving technology that offers a secure and convenient way to verify identities. From mobile devices to Banks, Government, Fintechs, its applications are vast and varied.
As the technology continues to advance, it is essential to address the challenges and ensure that face authentication systems are secure, accurate, and respectful of user privacy.
At Deepvue, we are committed to leveraging the latest advancements in face authentication to provide robust and reliable solutions for our clients. One such solution is our Face Match API.
The Face Match API is a powerful tool that accurately compares two images to determine if they belong to the same individual, making it ideal for security and identity verification applications. Whether you are looking to secure your financial transactions, control access to sensitive areas, or enhance the user experience, Deepvue’s Face Match API offers a reliable and efficient solution.
To learn more about how Deepvue’s Verification Suite can enhance your online identity verification process, visit Deepvue.tech and explore their range of APIs designed to ensure accuracy and efficiency.
FAQs
What is the difference between face authentication and face recognition?
Face authentication verifies a person’s identity by comparing their live facial image to a stored faceprint, ensuring they are who they claim to be. Face recognition, on the other hand, identifies a person by comparing their facial image to multiple faceprints in a database to determine who they are among a list of potential matches.
Is face authentication safe to use?
Yes, face authentication is generally safe to use. It relies on unique biological traits that are difficult to replicate or steal. Additionally, advanced face authentication systems incorporate anti-spoofing measures to prevent fraud using photos, videos, or masks. It is essential to use systems that comply with data protection regulations to ensure user privacy and data security.
Can face authentication work in low light conditions?
Modern face authentication systems are designed to work in a variety of lighting conditions, including low light. They use advanced algorithms and infrared technology to capture facial features accurately, even in dimly lit environments. However, extreme lighting conditions may still pose challenges, so optimal lighting is recommended for the best performance.
What happens if my appearance changes significantly?
Face authentication systems are built to accommodate minor changes in appearance, such as hairstyle changes, makeup, or glasses. For significant changes, such as facial injuries or major weight loss/gain, you may need to update your faceprint in the system to ensure continued accurate authentication. Regular updates help maintain the reliability of the system.
How does face authentication benefit Aadhaar users?
Face authentication enhances the security and convenience of the Aadhaar system by providing an additional layer of biometric verification. It allows users to authenticate their identity quickly and easily without physical documents or passwords. This is particularly beneficial for individuals who may have difficulties with fingerprint or iris scans, making the Aadhaar system more inclusive and user-friendly.








