Protecting sensitive information is crucial for businesses that deal with customer data. You might be a cloud service provider, SaaS firm, or any company dealing with client data – demonstrating your security controls are industry-compliant is the key. That’s where SOC 2 comes in.
Obtaining SOC 2 compliance involves a thorough audit from a third-party company, confirming that your company adheres to the necessary security standards. Though the process appears daunting, it ultimately benefits businesses by establishing trust, enhancing cybersecurity practices, and gaining a competitive advantage. This guide will simplify all you must understand what is SOC 2 compliance—why you should care, what it takes, and the best way to have your business become certified.
What is SOC 2 Compliance?
SOC 2 (System and Organization Controls 2) is a security standard created by the American Institute of Certified Public Accountants (AICPA). It is tailor-made for cloud and technology companies dealing with sensitive data. SOC 2 is established on five Trust Service Criteria (TSC) – security, availability, processing integrity, confidentiality, and privacy – that organizations must adhere to. To demonstrate compliance, an independent audit is required to be performed by them. There are two forms of SOC 2 reports: Type I, which addresses the design of security controls at a given point in time, and Type II, which addresses their operation over a period of time (typically 3-12 months). SOC 2 compliance helps organizations build customer trust, meet regulations, and prevent security breaches.
The Importance of Data Security for Service Organizations
Data security is vital to service organizations as they process tremendous volumes of confidential customer and business data. Preserving such information ensures trust is maintained, regulations are met, and losses resulting from breaches or cyberattacks are avoided. Service organizations frequently maintain personal, financial, and proprietary information, placing them in a high-risk zone for being attacked by hackers. A data breach can result in serious implications such as loss of reputation, penalties, and trust of customers.
Implementing strong cybersecurity measures, such as encryption, multi-factor authentication, and regular security audits, helps safeguard sensitive information from unauthorized access. Also, compliance with industry standards like GDPR, HIPAA, and ISO 27001 ensures that organizations are law-abiding and follow best practices for data protection.
Overview of Trust Services Criteria
- Security is the backbone of TSC and provides assurance that systems are safeguarded against unauthorized access, breaches, and vulnerabilities through sound controls like firewalls, encryption, and access control.
- Availability is concerned with system uptime and responsiveness so that services are running and available as per service level agreements (SLAs).
- Processing Integrity allows the system to process complete, accurate, and timely, error-free, without fraud or alteration of data.
- Confidentiality protects sensitive data from unauthorized release, where only allowed users can view it based on business requirements.
- Finally, Privacy dictates how personal data is collected, used, stored, and secured by relevant laws and regulations, ensuring transparency and user control of their information.
Differentiating Between SOC 2 Type 1 and Type 2 Reports
| Feature | SOC 2 Type 1 | SOC 2 Type 2 |
| Purpose | Evaluates the design and implementation of controls at a specific point in time. | Assesses the effectiveness of controls over a period of time. |
| Assessment Period | Single point in time. | Typically 3 to 12 months. |
| Focus | Ensures controls are properly designed and exist. | Verifies that controls are functioning effectively over time. |
| Use Case | Suitable for initial audits or new systems. | Preferred for demonstrating ongoing compliance and security commitments. |
| Level of Assurance | Provides a snapshot of security posture. | Offers a more comprehensive evaluation of security practices. |
The Role of the American Institute of CPAs (AICPA)
The American Institute of Certified Public Accountants (AICPA) has a significant role in establishing professional standards, promoting the accounting profession, and serving CPAs in the United States. As the largest association of Certified Public Accountants (CPAs), the AICPA establishes auditing, ethics, and quality control standards for public and private companies, nonprofit organizations, and government agencies.
It also works together closely with such government agencies as the Financial Accounting Standards Board (FASB) and the Securities and Exchange Commission (SEC) to help ensure financial reporting integrity. AICPA also provides educational resources, continuing professional education (CPE) courses, and certification examinations, such as the Uniform CPA Examination. It also speaks for accounting professionals through involvement in policy discussions and advocating best practices in financial management, auditing, and taxation.
Steps to Achieve SOC 2 Compliance
- The first step is conducting a gap analysis, which helps identify areas where current security practices fall short of SOC 2 requirements. This means comparing current policies, procedures, and controls against the SOC 2 framework to identify what must be improved.
- After gaps are identified, the next action is applying the controls needed to fill those gaps. These controls can involve bolstering data encryption, enhancing access controls, tightening incident response plans, and providing strong security monitoring.
- Lastly, audit preparation entails collecting all required documentation, conducting internal readiness reviews, and verifying system performance as stipulated. Requesting an independent auditor to conduct a pre-assessment helps in detecting any last-minute discrepancies before the formal SOC 2 audit.
The Audit Process Explained
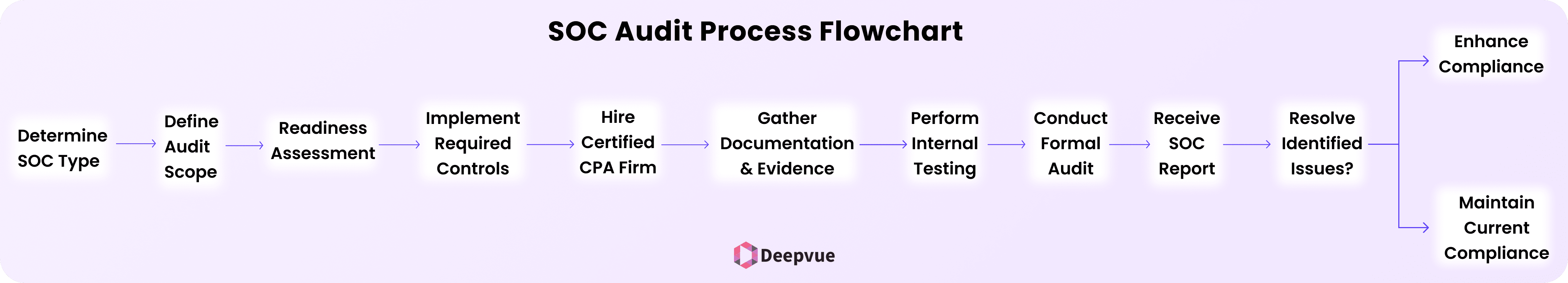
- Determine the SOC Type: Select SOC 1, SOC 2, or SOC 3 depending on your company’s needs and client demands.
- Define the Audit Scope: Identify systems, processes, and controls to be evaluated in the audit.
- Carry out a Readiness Assessment: Conduct an internal assessment or engage a consultant to determine gaps before the official audit.
- Implement Required Controls: Meet security, availability, processing integrity, confidentiality, and privacy (SOC 2 standards).
- Hire a Certified CPA Firm: Employ an accredited firm to conduct the SOC audit and issue the report.
- Gather Documentation & Evidence: Gather policies, security logs, access controls, and other evidence to show compliance.
- Perform Internal Testing: Internally test security controls to ensure that they are SOC compliant.
- Replace the Formal Audit: The auditor reviews policies, procedures, and security controls to assess compliance.
- Get a SOC Report: The auditor provides a SOC 1, SOC 2, or SOC 3 report of findings and compliance status.
- Resolve Any Identified Issues: If gaps are identified, take corrective measures to enhance compliance.
Benefits of SOC 2 Compliance
- Building Credibility and Trust: Shows concern for data safety, boosting customer trust, and enhancing business partnerships.
- Enhancing Security Posture: Facilitates effective security controls to minimize data breaches and unauthorized access risks.
- Competitive Edge in the Market: Makes your business stand out from competitors by demonstrating adherence to industry-leading security standards, bringing more clients and partners.
Common Challenges in Achieving SOC 2 Compliance
It is hard to obtain SOC 2 compliance due to the intricacy of Trust Services Criteria (TSC) and the need for strong security policies. Organizations find it difficult to address third-party risks, implement stringent data security controls, and ensure continuous monitoring and logging. Employee training, availability of resources, and document burdens make it all the more cumbersome. Ongoing compliance post-certification continues to demand upgrades and audits throughout. Auditor expectation handling can even be challenging at first, especially when it’s for the initial time.
Conclusion
SOC 2 compliance is not just a security requirement—it’s a key to building trust with customers and ensuring your company is following best practices for data security. By complying with the five Trust Service Criteria and passing a rigorous audit, companies can prove their dedication to security, confidentiality, and reliability.
If your company is interested in simplifying security compliance and verification processes, visit Deepvue.tech for a complete verification API toolkit, with which you can easily meet compliance needs.
FAQs
What is SOC 2 compliance?
SOC 2 compliance is a security standard created by the AICPA that guarantees companies process customer information securely. It revolves around five Trust Service Criteria—security, availability, processing integrity, confidentiality, and privacy.
What are the 5 SOC 2 principles?
The five principles or Trust Service Criteria are security (defense against unauthorized access), availability (preservation of systems in a working state), processing integrity (trustworthy processing of data), confidentiality (limited data access), and privacy (protection of personal data).
What industries gain most from SOC 2 compliance?
Such companies handling sensitive customer data, for instance, technology, cloud computing, healthcare, finance, and SaaS providers, are served best by it. It helps such companies maintain security levels and gain customer trust.
How frequently should a SOC 2 audit be conducted?
The SOC 2 audit must be repeated annually so that compliance is ensured to be a continuous process. Yearly audits help companies to ensure security measures are updated to date and any loopholes filled,
How does SOC and SOX compliance differ?
SOC 2 is more concerned with the privacy and security of data for service providers, whereas SOX is an American act that guarantees correct financial reporting in public companies.








