Transaction monitoring is also important in identifying and preventing financial crimes like money laundering and fraud. In the context of Anti-Money Laundering (AML) compliance, it entails ongoing monitoring of customer transactions to detect suspicious activity. AML transaction monitoring can be unusual money transfers, irregular shifts in spending habits, or big cash deposits.
Banks employ advanced formulas and machine learning algorithms to observe transactions in real-time. The systems identify activity that varies from a set baseline, triggering additional scrutiny. The ultimate goal is to detect illicit financial activity with as few false positives as possible.
What is Transaction Monitoring?
Transaction monitoring refers to reviewing, analyzing, and evaluating financial transactions in an attempt to uncover possible suspicious actions that might lead to money laundering, terrorism finance, or any other financial crimes. Transaction monitoring deals with the constant or batch process tracking of transactions aimed at looking out for deviating behavior relative to rules or patterns predefined earlier.
Key components of a transaction monitoring system include:
- Data Collection: Aggregating data from multiple sources, such as customer transactions, account information, and external databases.
- Risk Scoring: Allocating risk scores to transactions and customers by considering characteristics such as the size of the transaction, frequency, and geography.
- Alert Generation: Activating alerts against predefined rules or risk levels.
- Case Management: Researching alerts to ascertain the validity of suspicious transactions.
- Reporting: Reporting increasing confirmed suspicious transactions to regulatory bodies via Suspicious Activity Reports (SARs).
AML Transaction monitoring can be conducted in two primary ways:
- Real-Time Monitoring: Transactions are reviewed as they occur, allowing for immediate detection and response to suspicious activities.
- Batch Monitoring: Transactions are reviewed on a periodic basis, usually at the close of a business day or week, to detect anomalies in aggregate data.
Why is Transaction Monitoring Important in AML?
- Detecting Suspicious Activities: AML transaction monitoring systems are programmed to alert to unusual patterns, like abrupt large cash deposits, payments to high-risk locations, or a series of small transactions aimed at evading detection (smurfing).
- Regulatory Compliance: Banks are required by law to have in place effective AML programs, such as transaction monitoring, to meet regulations imposed by regulatory bodies such as the Financial Action Task Force (FATF), the Financial Crimes Enforcement Network (FinCEN), and the European Union’s AML Directives.
- Preventing Financial Crime Risks: Early identification of suspicious behavior enables financial institutions to initiate preventive measures, e.g., freeze accounts or block transactions, preventing financial risks.
- Protecting Institutional Reputation: Participation in money laundering can result in substantial fines, legal penalties, and reputational loss. Good AML transaction monitoring serves to prevent these risks.
How Does Transaction Monitoring Work?
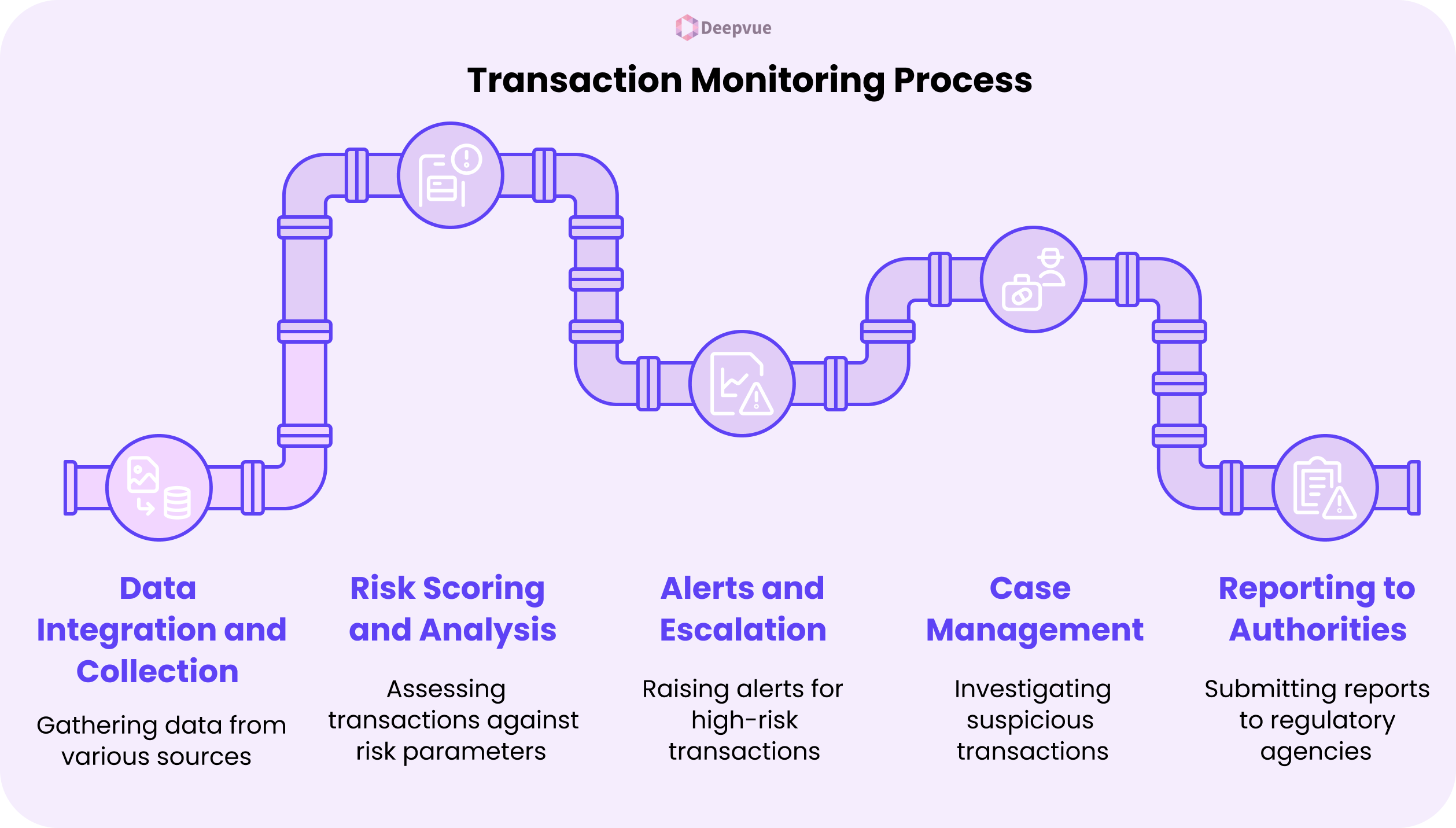
- Data Integration and Collection:
Information from multiple sources, such as bank accounts, payment gateways, and transaction logs, is aggregated for analysis.
Data points can range from transaction sizes, customer details, locations, and frequency of transactions.
- Risk Scoring and Analysis:
Each transaction is assessed against pre-set risk parameters.
Customers are rated based on the history of transactions, geographic locations, and activity in accounts.
- Alerts and Escalation:
When a transaction crosses pre-set risk levels, the system raises an alert.
Analysts evaluate these alerts to determine their authenticity, cross-verifying customer and transaction information.
- Case Management:
Verified suspicious transactions are raised as cases for additional investigation.
The investigators examine the account activity, transaction history, and customer profile to ascertain if the activity is truly suspicious.
- Reporting to Authorities:
Once a suspicious transaction is verified, financial institutions have to report a Suspicious Activity Report (SAR) to the applicable regulatory agency.
This report consists of complete details regarding the transaction, customer, and possible risk factors.
Common Techniques and Technologies in AML Transaction Monitoring
- Rule-Based Monitoring: Predefined rules are set based on regulatory guidelines or historical data. Examples of rules include alerting for transactions above a threshold or sequential transactions over a given period of time.
- Machine Learning and AI: Sophisticated systems use AI and machine learning to process transaction patterns and detect anomalies without being programmed explicitly. The systems learn from historical transactions and refine their detection criteria over time, increasing precision and minimizing false positives.
- Pattern Matching and Anomaly Detection: Historical transaction data can be used by systems to determine normal patterns of transactions and highlight deviations as suspicious. For example, if a consumer who normally does low-value transactions within the home country suddenly sends a big cross-border transfer, the system could mark it as suspicious.
- Real-Life Examples of AML Transaction Monitoring Systems: NICE Actimize, FICO, and SAS are some companies that offer advanced transaction monitoring systems with the help of AI and predictive analytics to identify sophisticated financial fraud.
Challenges in AML Transaction Monitoring
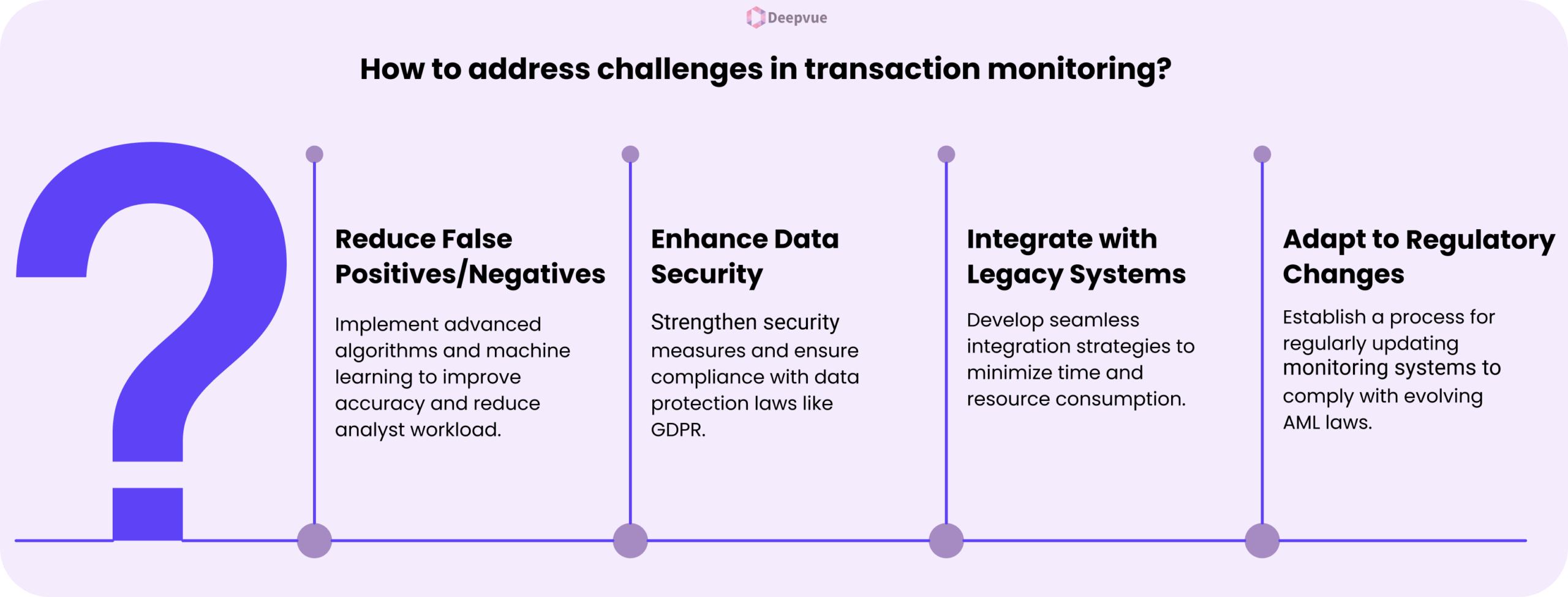
- False Positives and Negatives: Systems can produce too many false positives, inundating analysts and diminishing the attention to actual threats. On the other hand, false negatives happen when suspicious transactions are not detected, bringing regulatory and financial risks.
- Data Security and Privacy: Monitoring solutions call for access to confidential customer information, which creates data security and data protection law compliance issues such as GDPR.
- Integration with Legacy Systems: Merging new transaction monitoring products with legacy systems is often time- and resource-consuming.
- Shifting Regulatory Environment: AML laws are constantly changing, and institutions must revise monitoring systems and processes on a periodic basis.
Best Practices for Effective Transaction Monitoring
- Implement Risk-Based Approaches: Tailor monitoring thresholds and rules based on customer risk profiles, transaction types, and geographical regions.
- Harness Advanced Analytics and Automation: Employ machine learning and AI to identify subtle patterns and lower false positives.
- Periodically Revise Rules and Thresholds: Ongoingly update monitoring parameters according to surfacing threats as well as emerging regulatory guidelines.
- Organize Regular Training and Awareness Programs: Train employees to identify and respond to suspicious behavior effectively.
- Keep Strong Data Privacy and Security Measures: Utilize strong encryption, access restrictions, and anonymization of data to protect customer information.
Conclusion
Transaction monitoring is a vital component of effective AML programs, enabling financial institutions to detect, prevent, and report suspicious activities promptly. Through the use of advanced technologies such as AI, machine learning, and data analytics, institutions can improve their monitoring systems, minimize false positives, and correctly detect potentially illicit activities.
For fintech companies and banking institutions, the implementation of specialized APIs can greatly enhance the efficiency of anti-money laundering transaction monitoring. Deepvue.tech provides multiple APIs that totally work in line with AML compliance needs:
- Bank Statement Analysis API: Employs Optical Character Recognition (OCR) to pull and examine information from bank statements, giving insights into earning patterns, spending habits, and possible abnormalities. The analysis is critical in identifying suspicious transactions and evaluating customer risk profiles accurately.
- Document Verification APIs: Facilitate real-time verification of different identification documents such as Aadhaar, PAN, and passports. Proper identity verification is the foundation of AML compliance, whereby institutions must have a comprehensive knowledge of their customers’ identities.
FAQ
What is transaction monitoring in AML?
Transaction monitoring is the process of checking and examining financial transactions to identify possible money laundering, fraud, or other suspicious transactions. Transaction monitoring assists financial institutions in adhering to AML regulations and avoiding financial crimes.
Why should financial institutions pay attention to transaction monitoring?
It allows for financial institutions to detect unusual patterns or anomalies that might reflect money laundering, terrorist financing, or fraud, thus insulating them from regulatory penalties and reputation loss.
How does a transaction monitoring system operate?
Transaction monitoring systems gather transaction information, evaluate risk according to pre-established rules or machine learning models, trigger alerts for suspicious transactions, and escalate verified cases for investigation and reporting.
What are some typical red flags in transaction monitoring?
Red flags are large cash deposits, small transactions in batches (smurfing), transactions with high-risk jurisdictions, and unusual account activity not consistent with the customer’s profile.
What technologies do transaction monitoring systems use?
Contemporary systems take advantage of AI, machine learning, data analytics, and pattern recognition to identify anomalies, minimize false positives, and improve overall monitoring accuracy.








