Nowadays, security breaches are far more common than ever, and traditional security models are not enough. In this situation, the Zero Trust security model proves to be effective. This model fundamentally changes how organizations handle security by adopting the principle of “never trust, always verify.” The heart of this model is identity verification, an important safety measure to prevent unauthorized access by users and devices to valuable resources.
In this blog, we will explore how ID verification plays a crucial role in zero trust security and why it is indispensable for modern organizations.
Core Principles of Zero Trust Architecture

- Explicit Verification of Users
Each user or device in the zero trust architecture undergoes verification to grant access to sensitive resources. This approach has no room for implicit users because all users are authenticated and authorized. Mechanisms such as MFA and real-time validation of identities are used to minimize ransomware, insider threats, and data breaches. It enforces strict verification rules to secure your company’s cybersecurity architecture and protect the assets and data.
- Least Privilege Access
In the zero trust model, access to users is granted based on their roles, minimizing the attack surface. It offers minimum access to the users to remove risks of unauthorized access and data breaches. Access provided to the users is constantly reviewed and updated to ensure that the needs of the organization are aligned with the security policies. This principle ensures that when a breach occurs the potential damage is contained.
- Continuous Monitoring of Activities
The architecture of Zero Trust is real-time, which catches any suspicious activities by following each user’s behavior and the system. It logs these activities to the identities of anomalies and possible threats. These patterns are analyzed by the zero trust model, by using sophisticated algorithms and automated tools. This ensures that security measures evolve in tune with emerging threats. In addition, it ensures the retention of operational efficiency by offering a strong defense.
Key Components of Zero Trust Security
- Identity Verification: Continuously verifies the identity of the user and the legitimacy of the device.
- Multi-factor Authentication: Adds a layer of security beyond passwords.
- Granular Access Controls: Safe and controlled access to resources for different user roles.
- Behavior-Based Analytics: Access to resources is granted based on the roles of users.
Integration of Identity Management and Access Control
Integrating Identity Management with Access Control is key to Zero Trust Security. It brings focus to the integration of identity management with access control. This focus is aimed at continued verification of the identity and context of the user so that access requests are always in agreement with strict access controls and organizational policies.
Identity management is concerned with user provisioning, identity verification, and role-based access control (RBAC). The processes help manage user identities in the organization. For identity and biometric verification, businesses can leverage services like passive liveness and face match to add another layer of security to verify users. Attribute-based access control (ABAC), and policy enforcement points (PEPs) enforce decisions based on verified identities.
To implement Zero Trust, assess the current identity infrastructure and design an identity-centric architecture. This will integrate identity management into a Zero Trust framework. Continuous monitoring helps address potential threats. It authenticates access attempts against stringent access policies.
Regular audits and adjustments are necessary to manage and enforce these complex policies. This is vital across varying IT environments. By doing so, companies can protect sensitive resources and reduce their attack surface.
Key Components
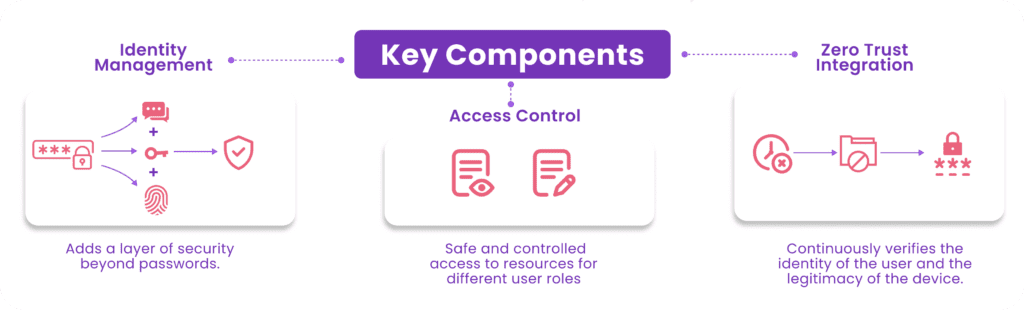
- Identity Management: It requires authorized people to gain access to resources. This includes robust user provisioning to manage user accounts effectively. Additionally, real-time verification methodologies such as role-based access control and multi-factor authentication assign permission based on specific roles. This will eventually reduce exposure to the organization while making users accountable.
- Access Control: The zero trust model utilizes ABAC and PEP techniques to enforce access control. ABAC aims to provide the user access based on the user’s attributes like the device type, role, and location. All these attributes affect the decision to access. PEP checks all the requests for access through security policies before providing access to a resource. Such fine-grained control is fundamental to a secure environment.
- Zero Trust Integration: A comprehensive framework integrates continuous verification and regular security audits. Continuous verification allows authentication in real-time of all access requests, regardless of any past access approvals. The regular security audit keeps the system robust to changing threats by identifying and addressing vulnerabilities. This integration fosters a proactive security posture, maintaining trust and compliance throughout the organization.
Challenges in Implementing Zero Trust Security
- Legacy system integration
The most challenging aspect is to integrate Zero Trust principles into legacy systems. Older infrastructure does not have compatibility with more advanced authentication protocols or fine-grained access controls. It is expensive and time-consuming to upgrade or retrofit these systems. Transition risks are also accompanied by business operations, especially with legacy applications since the business is highly reliant on them.
- Complex Access Policy Management
Access management in a zero-trust environment is complicated. ABAC and RBAC demand detailed rules to be defined and maintained for every user and device. Ensuring that policies are accurate and consistent becomes unmanageable at times.
Best Practices for Implementing Zero Trust Security
- Conducting Risk Assessments: Start by analyzing the current security posture of an organization for potential vulnerabilities. Risk assessment informs and sets priorities for work areas that need attention immediately.
- Establishing Clear Access Policies: Explicitly define and implement policies for access to organizational needs. Apply concepts such as least privilege access and ABAC to ensure the user or device only access what they need. Properly documented policies make it easier to adapt to changing roles or technologies.
- Regularly Updating Security Protocols: In a world where cyber threats are evolving quickly, security measures must be updated regularly. This includes updating systems, patching vulnerabilities, and refining access policies based on new insights or incidents. Continuous monitoring and auditing ensure that the Zero Trust framework remains effective against emerging threats.
Enhancing Security Posture through Zero Trust
Micro-Segmentation
Micro-segmentation is the bedrock of Zero Trust. It provides granular access controls that prevent lateral movement within the network. With this, organizations can enforce strict boundaries by tailoring roles or behaviors. Micro-segmentation divides the entire network into small components which minimizes the impact of breach. It sustains the security of the organization by ensuring that unauthorized access to one segment does not compromise others.
Adaptive Authentication
Adaptive authentication introduces a smart and intelligent layer of security by adjusting authentication requirements in the context of a given access attempt. Its real-time analysis of devices, location, and behavior patterns decides the right type of security measure. This delivers a secure access experience by enhancing security without immolating user convenience.
Continuous Tracking
Zero Trust emphasizes ongoing vigilance and continuous monitoring of user activities and system behaviors. Organizations can identify and respond to possible threats in real time by monitoring all activities in their network. Advanced analytics and automated alerts enable proactive security measures, ensuring that suspicious activities are addressed before they escalate into significant incidents.
Conclusion
Zero Trust Security assumes that no person, either inside or outside a network, should be trusted until verified. By embedding strong methods of verifying identity, businesses will ensure better protection of data, assure compliance, and keep the business’s data from unauthorized access.
Incorporating identity verification into a Zero Trust Security model is not just a best practice—it’s a necessity for protecting against cyber threats. Adopting Zero Trust will build a security-first culture that fosters trust, accountability, and safety across every level of any organization. For further details about how our identity verification solutions can advance your security framework contact us today.
FAQ:
What is Zero Trust Security?
Zero Trust is an identity-based security model that by default assumes no one, either inside or outside the organization, should be trusted. All accesses need to be verified before being allowed.
How does Identity Verification fit into Zero Trust?
Identity verification ensures that every user and device is authenticated before accessing resources, which is essential in a zero-trust model.
What challenges come with implementing Identity Verification in Zero Trust?
Challenges that may be encountered are user resistance, ease of use and security, and new integration with old infrastructure.
How does Zero Trust protect against insider threats?
Zero Trust constantly authenticates users and behavior, reducing unauthorized access risk from a trusted insider.








