NFC (Near Field Communication) tags are playing a pivotal role to provide seamless connectivity in this digital era. These small yet powerful devices are revolutionizing how we interact with our gadgets and the world around us. In this article, we’ll explore what an NFC tag is, how it works, and how these apply in our daily lives.
What is RFID?
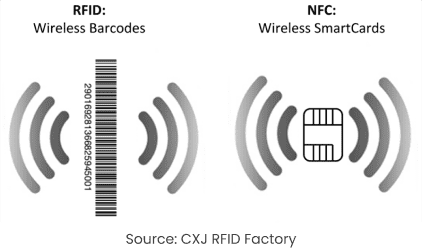
RFID (Radio Frequency Identification) is a wireless technology that uses electromagnetic fields to identify and track objects with tags containing stored data. RFID tags are commonly used in inventory management, access control, and logistics. Unlike NFC, which works over short distances, RFID can operate over longer ranges.
What is an NFC Tag?
NFC tag means a small but powerful piece of technology designed to enable seamless wireless communication between devices over short distances. These tags are usually embedded in a chip form and can be found in various items, from stickers and cards to smartphones and other smart devices.
NFC tags are incredibly versatile. They can store data, which can be read by an NFC reader, such as a smartphone. This data exchange allows for quick and efficient communication, making NFC tags ideal for applications where speed and convenience are paramount.
What is a Near Field Communication (NFC) Tag?
An NFC tag is a type of technology that facilitates wireless communication between devices over short distances, typically a few centimeters. These tags are usually embedded in a chip form and can be found in various items, from stickers and cards to smartphones and other smart devices.
NFC tags are incredibly versatile. They can store data, which can be read by an NFC reader, such as a smartphone. This data exchange allows for quick and efficient communication, making NFC tags ideal for applications where speed and convenience are paramount.
What is an NFC Reader?
An NFC reader is a device that reads and interacts with NFC tags or other NFC-enabled devices through a short-range wireless communication protocol. NFC readers are commonly found in smartphones, payment terminals, and security systems.
These readers facilitate various applications, such as:
- Contactless Payments: Enabling transactions through services like Google Pay, Apple Pay, and Samsung Pay.
- Data Sharing: Allowing quick sharing of files, URLs, or contact information.
- Access Control: Providing secure entry to offices or events using NFC-enabled ID cards.
- Inventory Management: Streamlining asset tracking in warehouses or stores with NFC tags on products.
NFC Tag Components
- Antenna: The antenna is a coiled wire that receives and transmits radio frequency signals to and from the NFC reader. It enables the tag to communicate with compatible devices within a short range.
- Microchip (IC): The integrated circuit (IC) is the core component that stores data, processes commands, and manages data exchange. It includes memory storage, typically ranging from a few bytes to several kilobytes, depending on the tag type.
- Substrate: The substrate is the physical base that holds the antenna and microchip. It is usually made of plastic, paper, or other flexible materials to maintain the tag’s form factor.
- Power Source: Unlike active NFC devices, passive NFC tags do not have a built-in power source. They rely on the electromagnetic field generated by the NFC reader to power the microchip and facilitate data transfer.
How Does an NFC Tag Work?
NFC tags are composed of two main components: a copper coil and a microchip. Here’s a step-by-step look at how they operate:
- Proximity Activation: When an NFC reader, such as a smartphone, comes within a close range (typically around four inches) of an NFC tag, it initiates the communication process.
- Electromagnetic Induction: The NFC reader emits a signal that is captured by the copper coil in the NFC tag. This signal generates a small electrical current in the coil.
- Powering the Microchip: The generated current powers the microchip in the NFC tag. This microchip is where the data is stored.
- Data Transmission: The microchip uses this power to transmit its stored data back to the NFC reader via inductive coupling.
- Data Processing: The NFC reader receives the data and can then process it according to the specific application. This entire interaction happens in mere seconds, making NFC tags a quick and efficient way to handle data.
Types of NFC Tags
NFC tags come in different types, each suited for various applications based on their memory capacity, data transmission speed, and usability. Here are the five commonly accepted types:
- Type 1: Offers 90-454 bytes of space and a transmission speed of 106 kilobits per second. These are often used in special-purpose applications.
- Type 2: Provides 40-140 bytes of space with a similar transmission speed to Type 1. These are general-purpose chips.
- Type 3: Has a larger capacity, with 200-3,000 bytes of space and a speed of 200-400 kilobits per second. Specific-use chips often fall into this category.
- Type 4: Features 1,500-7,500 bytes of space and a transmission speed of 100-400 kilobits per second. These are secure-use chips.
- Type 5: Offers the largest capacity with 30-8,000 bytes of space and a speed of around 400 kilobits per second. These are typically used in industrial applications.
Can You Rewrite an NFC Tag?
Yes, NFC tags can be rewritten, but it depends on the type of tag and its current configuration. By default, most NFC tags are writable, allowing users to store or update data such as URLs, contact information, or commands. Rewriting can be done using NFC-enabled smartphones or specialized NFC writing apps.
However, some tags come with a write-protection option, which, once enabled, locks the tag and prevents further modifications. This feature is often used for security purposes to ensure data integrity. If you’re using NFC tags for temporary events or dynamic data, keeping them rewriteable is beneficial. On the other hand, for sensitive or permanent information, enabling write protection ensures data security.
Practical Applications of NFC Tags
The practicality and versatility of NFC tags have led to their widespread adoption in various fields. Here are some notable examples:
- Contactless Payments: One of the most common uses of NFC tags is in tap-to-pay systems. These systems allow users to make secure transactions simply by bringing their NFC-enabled device close to a payment terminal.
- Access Control: Many workplaces and secured areas use NFC tags embedded in ID cards to control access. These tags ensure that only authorized personnel can enter restricted zones.
- Public Transport: NFC tags are often used in transit systems to provide a seamless way for passengers to pay fares and access services.
- Smart Posters: NFC tags embedded in posters can provide additional information to users who tap their smartphones against the tag. This is a popular method for delivering promotional content and event details.
- Product Authentication: Companies use NFC tags to verify the authenticity of their products. Consumers can tap their phones against the tag to ensure they are purchasing a genuine item.

Benefits of Using NFC Tags
NFC technology has gained prominence due to its numerous benefits:
- Convenience: NFC tags provide a quick and easy way to transfer data without needing to physically connect devices. This convenience is particularly evident in contactless payment systems.
- Versatility: The applications of NFC tags are vast, ranging from secure payments and access control to smart posters and product authentication.
- Cost-Effective: Implementing NFC technology is relatively inexpensive, especially considering the benefits it brings. The tags themselves are small and require minimal power to operate.
- Security: NFC tags can be encrypted, making them a secure way to handle sensitive information such as payment details and personal identification.
NFC Tags vs. RFID Tags
NFC tags are often compared to RFID (Radio Frequency Identification) tags, as both technologies use radio waves to communicate. However, there are key differences:
- Range: RFID tags can communicate over longer distances than NFC tags. While NFC is designed for close-proximity communication, RFID can work from several meters away.
- Complexity: NFC allows for two-way communication, meaning devices can exchange information. In contrast, RFID typically involves one-way communication from the tag to the reader.
- Applications: Due to their range, RFID tags are often used in logistics and inventory management, whereas NFC is preferred for applications requiring close-range interaction, like payments and access control.
How to Use NFC Tags with Your Phone
Most modern smartphones are equipped with NFC capabilities, allowing them to read and interact with NFC tags. Here’s how you can enable NFC on your device:
On Android
- Go to Settings: Open your phone’s settings menu.
- Connected Devices: Navigate to ‘Connected Devices’.
- Connection Preferences: Tap on ‘Connection Preferences’.
- Enable NFC: Find and enable the NFC option.
On iPhone
- Go to Settings: Open the settings menu.
- Control Center: Tap on ‘Control Center’.
- More Controls: Under ‘More Controls’, find and add the NFC tag reader.
- Activate NFC: Your iPhone should now be able to read NFC tags when it is within range.
Conclusion
NFC tags are a simple yet powerful technology that enhances our interaction with the digital world. From facilitating secure payments to providing quick access to information, the applications are diverse and growing.
As NFC technology continues to evolve, we can expect even more innovative uses that will make our lives easier and more connected.
At Deepvue, we’re excited about the possibilities NFC technology brings and are committed to leveraging it to create smarter, more efficient systems for our clients.
To learn more about how Deepvue’s Verification Suite can enhance your verification processes, visit Deepvue.tech and explore their range of APIs designed to ensure accuracy and efficiency.
FAQs
What is an NFC tag used for?
NFC tags are used for a variety of applications, including contactless payments, access control, product authentication, public transport ticketing, and smart posters. They allow for quick and secure data transfer between devices over short distances.
How do I know if my phone can read NFC tags?
Most modern smartphones come with built-in NFC capabilities. To check if your phone has NFC, go to your device’s settings and look for the NFC option under connectivity settings. If it’s available, you can enable it and start using your phone to read NFC tags.
Are NFC tags secure?
Yes, NFC tags can be secure. They can be encrypted to protect the data they store. However, like any technology, they are susceptible to certain security risks such as cloning and phishing attacks. It’s important to use NFC tags from reputable sources and keep your devices updated with the latest security patches.
Can NFC tags be rewritten?
Some NFC tags are rewritable, which means you can change the data stored on them multiple times. Others are read-only and can only be written only once. The type of NFC tag you choose depends on your specific needs and application.
What is the difference between NFC and Bluetooth?
NFC and Bluetooth are both wireless communication technologies, but they serve different purposes and operate over different ranges. NFC works over very short distances (a few centimeters) and is typically used for quick, secure transactions and data exchanges.
Bluetooth, on the other hand, works over longer distances (up to 100 meters) and is commonly used for continuous data streaming, such as audio and file transfers. NFC is often more secure for short-range interactions, while Bluetooth is better suited for sustained connections.








