Identity theft is a serious crime that involves the unauthorised acquisition and use of someone’s personal or financial information for fraudulent purposes. In today’s digital age, personal information is more accessible, making identity theft a prevalent and damaging crime. This article explores the different types of identity theft, including credit card fraud, child identity theft, and synthetic identity theft, and provides strategies to protect yourself and recognize the signs of identity compromise.
Understanding Identity Theft
Identity theft occurs when someone obtains and uses another person’s personal information without their consent for financial gain. This information can include the victim’s name, birth date, Social Number, address, or credit card details. With this stolen information, identity thieves impersonate their victims to interact with various institutions and businesses, using a false identity to benefit themselves financially. Thieves employ tactics such as physical theft, diving into garbage, data skimming, hacking mobile devices, and social engineering schemes. Additionally, large-scale data breaches often provide a wealth of personal information for identity theft schemes. Complicating matters further, individuals sometimes willingly collaborate with others, sharing linked accounts for evasive financial activities.
What Happens When Your Identity Is Stolen?
Identity theft can have devastating consequences for both individuals and organisations. Victims may face financial loss, damage to their reputation, and legal repercussions if their stolen identity is used for criminal activities. Data breaches and identity theft also pose a significant threat to businesses, resulting in financial losses and reputational damage. It is a global concern that highlights the risks associated with technological advancements that can be exploited by cybercriminals.
How Does Identity Theft Happen?
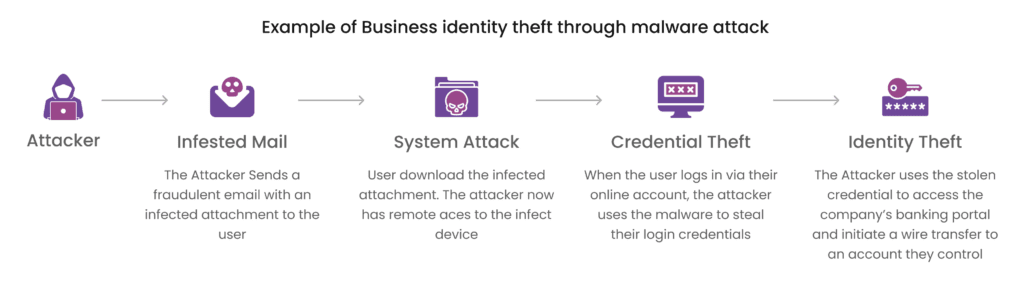
Identity theft can occur through physical and digital channels. Thieves may physically steal wallets to access credit cards or use technological tactics like phishing scams and malware to commit online theft. Unsecured Wi-Fi networks, weak password management, and corporate data breaches provide vulnerabilities for identity thieves to exploit in the digital realm. Once they have someone’s personal information, criminals can open new accounts, make unauthorised purchases, access confidential data, or file fraudulent tax returns. The increase in digital activity, accelerated by the pandemic, has led to a surge in identity theft incidents, emphasising the importance of constant vigilance.
Types of Identity Theft
Identity theft encompasses various types, each with its own challenges and methods. These include:
- Social Security Number Identity Theft: Thieves use someone’s Social Security number to apply for credit, benefits, and fraudulent tax refunds.
- Medical Identity Theft: Personal information is stolen to access medical services, prescriptions, or make fraudulent insurance claims.
- Credit Card Identity Theft: Criminals access credit card information or online retail accounts to make unauthorised transactions.
- Child Identity Theft: Children are vulnerable targets, and thieves can use their Social Security numbers to open fraudulent accounts or apply for loans.
- Synthetic Identity Theft: Thieves combine real and fabricated information to create new identities that are difficult to detect.
- Financial Identity Theft: Illegal access and use of bank, credit, or financial accounts, resulting in financial loss and credit damage.
- Criminal Identity Theft: When criminals impersonate someone else during an arrest or investigation, leading to false accusations and wrongful criminal records.
- Tax Identity Theft: Impostors use stolen personal information to file tax returns in someone else’s name, causing problems with tax authorities.
Examples of Identity Theft
Consider the case of Sarah, whose personal information was stolen in a data breach. She becomes a victim of multiple types of identity theft:
- Financial Identity Theft: The thief uses Sarah’s bank account information to open new credit card accounts and make unauthorised purchases.
- Medical Identity Theft: The thief uses Sarah’s personal information to receive medical treatments and services under her name.
- Child Identity Theft: The thief uses Sarah’s child’s information to open fraudulent accounts and apply for loans.
Sarah must take immediate action to report the fraud, dispute false accounts, and protect her and her child’s identities.
How to Report Identity Theft & Recover from Fraud?
- Check your bank and credit card statements for unfamiliar transactions.
- Watch for unexpected bills, debt collection calls, or denied credit applications.
- Report identity theft to the FTC at IdentityTheft.gov.
- File a police report if required by creditors or for criminal fraud cases.
- Contact Experian, Equifax, and TransUnion to place a fraud alert or credit freeze.
- Notify your bank, credit card company, and lenders of fraudulent activity.
- File IRS Form 14039 if you suspect tax-related identity theft.
- Contact the Social Security Administration if your SSN is compromised.
- Change all passwords and enable multi-factor authentication (MFA) on important accounts.
- Freeze or lock your credit to prevent unauthorized accounts.
- Monitor your credit reports regularly at AnnualCreditReport.com.
- Update security settings for your email, financial, and shopping accounts.
- Request fraud investigations and obtain written confirmation of fraudulent activity.
- Close or replace compromised accounts immediately.
- Shred sensitive documents before disposing of them.
- Be cautious of phishing scams and avoid clicking suspicious links.
- Regularly review financial statements to detect any unauthorized transactions.
How to Protect Yourself from Identity Theft & Fraud
To protect yourself from identity theft, use strong passwords, enable two-factor authentication, and secure all devices with a password. Regularly monitor bank and credit card statements for unauthorised transactions. Organisations can enhance security measures by utilising advanced identity verification methods through APIs.
Preventing Identity Theft and Data Breaches
Organisations can prevent identity theft and data breaches by implementing employee training programs on cybersecurity, conducting phishing simulation exercises, and using multi-factor authentication with biometrics for customer identity verification. Solutions like identity verification APIs can greatly enhance fraud prevention strategies and protect customers from identity theft.
Conclusion:
In conclusion, identity theft is a serious threat that businesses need to address in order to protect their customers and their own reputation. By implementing comprehensive identity theft prevention programs, following global regulations, and investing in employee training and technology solutions, businesses can significantly reduce the risk of falling victim to fraudsters. At Deepvue, we offer a range of identity verification solutions to help businesses safeguard their users from identity theft. Contact us today to learn more about how our solutions can help protect your business and your customers. Stay one step ahead of fraudsters and ensure a secure digital environment for all.
Contact us today for a demo of our identity verification solutions. Stay safe, stay secure with Deepvue.