Ensuring the authenticity of an individual’s identity is crucial for various online and offline transactions. Identity verification helps prevent fraud, maintain security, and build trust between businesses and their customers.
But what exactly is identity verification, and how does it work? This comprehensive guide will walk you through the process in a simple and easy-to-understand manner.
What is Digital Identity Verification?
Digital identity verification is a process that confirms whether a person is who they claim to be by verifying the authenticity of the documents. This process involves checking official documents, biometric data, and other identifiers to authenticate an individual’s identity. By doing so, it helps mitigate risks associated with identity theft, fraud, and unauthorized access.
Why is Identity Verification Important?
Identity verification plays a pivotal role in various sectors, including finance, healthcare, e-commerce, and more. It ensures that:
1. Security is Maintained: Prevents unauthorized access to sensitive information.
2. Fraud is Minimized: Reduces the risk of identity theft and financial fraud.
3. Compliance is Met: Helps businesses comply with regulatory requirements.
4. Trust is Built: Enhances customer trust and credibility.
How Does the Identity Verification Process Work?
The identity verification process involves several steps to ensure accuracy and security. Here’s a breakdown of the common methods used:
1. Document Verification:
- ID Document Submission: The individual submits a government ID, such as a passport, driver’s license, aadhaar, or national ID card.
- Data Extraction: The verification system extracts and analyzes information from the submitted document.
- Authenticity Checks: The system checks for security features like watermarks, holograms, and microprints to verify the document’s authenticity.
2. Biometric Verification:
- Facial Recognition: The individual takes a selfie or a live photo, which is then compared to the photo on the ID document.
- Fingerprint Scanning: Some systems may require a fingerprint scan to match against stored biometric data.
- Iris or Retina Scanning: Advanced systems may use eye scans for higher accuracy.
3. Database Cross-Referencing:
- Data Matching: The information is cross-referenced with trusted databases to ensure consistency and accuracy.
- Fraud Detection: The system checks for any signs of fraud or manipulation in the submitted data.
4. Liveness Detection:
- Active Liveness: The individual may be asked to perform specific actions, like blinking or turning their head, to prove they are physically present.
- Passive Liveness: The system automatically detects signs of life from the submitted photo or video.
How Digital Identity Verification Works?
With the rise of digital transactions, online identity verification has become increasingly important. This process is similar to in-person verification but is conducted entirely online. Here’s how it works:
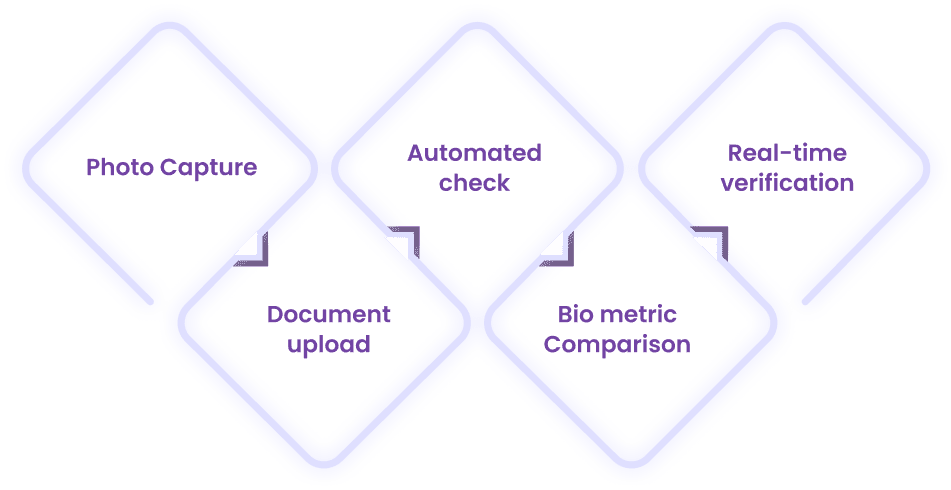
- Photo Capture: The individual captures a photo of their ID document and a selfie.
- Document Upload: Both the ID document and the selfie are uploaded to the verification platform.
- Automated Checks: The platform performs automated checks on the uploaded documents and photos.
- Biometric Comparison: Facial recognition technology compares the selfie with the photo on the ID document.
- Real-Time Verification: The entire process is completed in real-time, providing instant verification results.
Common Methods Used for Identity Verification
- Facial Recognition: Compares facial features from a live photo or selfie with the ID document photo.
- Fingerprint Scanning: Matches the individual’s fingerprint with stored biometric data.
- Document Verification: Checks the authenticity of submitted documents using security features.
- Liveness Detection: Ensures the person is physically present during the verification process.
- Database Cross-Referencing: Verifies information against trusted databases for consistency.
Identity Verification vs. Identity Authentication
While the terms “identity verification” and “identity authentication” are often used interchangeably, they refer to different processes with separate purposes. Understanding the differences between these two concepts is crucial for implementing effective security measures.
Identity Verification
Identity verification is the process of confirming that an individual is who they claim to be. It involves checking and validating the information provided by a person against trusted sources or databases. This process typically occurs at the initial stage of onboarding or registration and includes steps like:
- Document Verification: Checking the authenticity of government ID documents.
- Biometric Verification: Comparing biometric data such as facial features or fingerprints with those on records.
- Database Cross-Referencing: Matching the information provided with records in trusted databases.
The primary goal of identity verification is to establish a person’s identity with a high level of confidence to prevent fraudulent transactions and unauthorized access.
Identity Authentication
Identity authentication, on the other hand, is the process of confirming that a person accessing a service or system is a verified individual. This ongoing process typically follows identity verification and involves cross-checking the identity each time the individual tries to access a resource. Common methods of identity authentication include:
- Password Authentication: Using a password that only the verified individual knows.
- Two-Factor Authentication (2FA): Combining something the individual knows (password) with something they have (a mobile device or a token).
- Biometric Authentication: Using biometric data like fingerprints, facial recognition, or voice recognition to grant access.
- Multi-Factor Authentication (MFA): Combining multiple authentication methods to enhance security.
The main purpose of identity authentication is to ensure that the person accessing a system or service is a verified individual, thereby maintaining security.
Why Identity Verification & Authentication are important?
Both identity verification and identity authentication are crucial components of a robust security strategy:
- Enhanced Security: Verification ensures that only legit users get initial access, and authentication maintains secure access over time.
- Fraud Prevention: Verification prevents fraudsters from gaining entry, and authentication ensures that previously verified individuals remain authorized users.
- Regulatory Compliance: Many regulations require both verification and authentication to protect sensitive information and ensure data privacy.
How ID Verification Software Prevents Identity Theft
Identity theft is very concerning, especially with the increasing adoption of online services. Here are some ways identity verification helps prevent identity theft:
- Strong Authentication: Multi-factor authentication methods, such as combining facial recognition with document verification, provide robust security.
- Real-Time Monitoring: Continuous monitoring and real-time verification help detect and prevent fraudulent activities.
- Data Encryption: Ensures that all personal data is encrypted and securely stored.
- Fraud Detection Systems: Advanced algorithms and machine learning techniques identify suspicious activities and potential fraud attempts.
What is Online Identity Verification?
Online identity verification is the process of confirming that a person is who they claim to be when accessing digital services. It uses technology to validate personal information, documents, or biometric data (like facial recognition or fingerprints) to ensure the individual’s identity is legitimate.
This process is commonly used by banks, fintech platforms, e-commerce websites, and government services to prevent fraud, comply with regulations (like KYC/AML), and secure online transactions. Methods can include document verification, OTP-based checks, selfie matching, database cross-referencing, and more.
How Are Biometrics Used for Identity Verification?
Biometric data, such as fingerprints, facial features, and iris patterns, are unique to each individual, making them highly reliable for identity verification. Here’s how biometrics are used:
- Fingerprint Scanning: Scans and matches fingerprints with stored data.
- Facial Recognition: Compares facial features from a live photo or video with the ID document photo.
- Iris and Retina Scanning: Uses unique patterns in the eye for high-accuracy verification.
- Palm Recognition: Analyzes the unique patterns of veins in the palm.
Use Cases for Digital Identity Verification Solutions
Identity verification solutions encompass a variety of processes and technologies designed to authenticate individuals and prevent fraud. These solutions are widely used across different industries, including:
- Financial Services: Banks and financial institutions use identity verification to prevent fraud and comply with regulations.
- E-Commerce: Online retailers verify customers’ identities to prevent fraud and ensure secure transactions.
- Healthcare: Medical institutions use identity verification to protect patient data and ensure accurate records.
- Travel and Hospitality: Airports and hotels use identity verification to enhance security and streamline check-in processes.
- Telecommunications: Telecom companies verify identities to prevent fraud and ensure secure communication services.
The Future of Identity Verification Services and Digital Identity Verification
- Digital identity verification will become faster, smarter, and more seamless with AI and machine learning.
- Biometric authentication methods like facial recognition and fingerprint scans will see wider adoption.
- Governments and businesses will increasingly adopt digital ID frameworks like India’s Aadhaar or the EU’s eIDAS.
- Identity verification will shift toward continuous and behavioral authentication instead of one-time checks.
- Decentralized identity models using blockchain will give users more control over their personal data.
Conclusion
Digital identity verification is a critical process in today’s digital world. By leveraging advanced technologies and robust methods, it ensures that individuals are who they claim to be, thus preventing fraud, enhancing security, and building trust.
Whether conducted online or offline, identity verification plays a vital role in safeguarding personal information and maintaining the integrity of various transactions and services.
Understanding how identity verification works and its importance can help individuals and businesses make informed decisions about their security measures. As technology continues to evolve, so will the methods and solutions for identity verification, making it an ever-important aspect of the digital lives.








