Digital security would be incomplete without public key infrastructure (PKI). Specifically, it refers to a collection of policies, software, hardware and procedures that underlie the creation, management, distribution, use and revocation of digital certificates. Digital certificates are important in facilitating secure electronic transactions and communications.
The growing need for secured online transactions in this digital transformation makes PKI important. At Deepvue.tech we appreciate the value of strong security systems for financial integrations as well as insights and therefore PKI forms part of what we offer.
What is Public Key Infrastructure (PKI) & How Does It Work?
At its foundation level PKI uses cryptographic keys for data transmission securities over networks. These keys consist of two parts; public key and private key. The former can be accessed by anyone while the latter is hidden from view. This method called asymmetric encryption ensures that only verified & intended recipients can retrieve encrypted data.
How PKI Works
- Public Key Generation– First, a public key is created by a trusted body called a Certificate Authority (CA). Then, this public key is linked to a digital certificate.
- Private Key Generation– In addition to the public key, an accompanying private key is created too. This remains confidential and used by the receiver to decode the data.
- Certificate Authority (CA)– The digital certificates are given by trusted CA. These certificates verify who is requesting it and link them with its public key.
- Digital Certificates – They help prove the authenticity of their owners’ identities and can be used to securely enable communication between multiple parties involved.
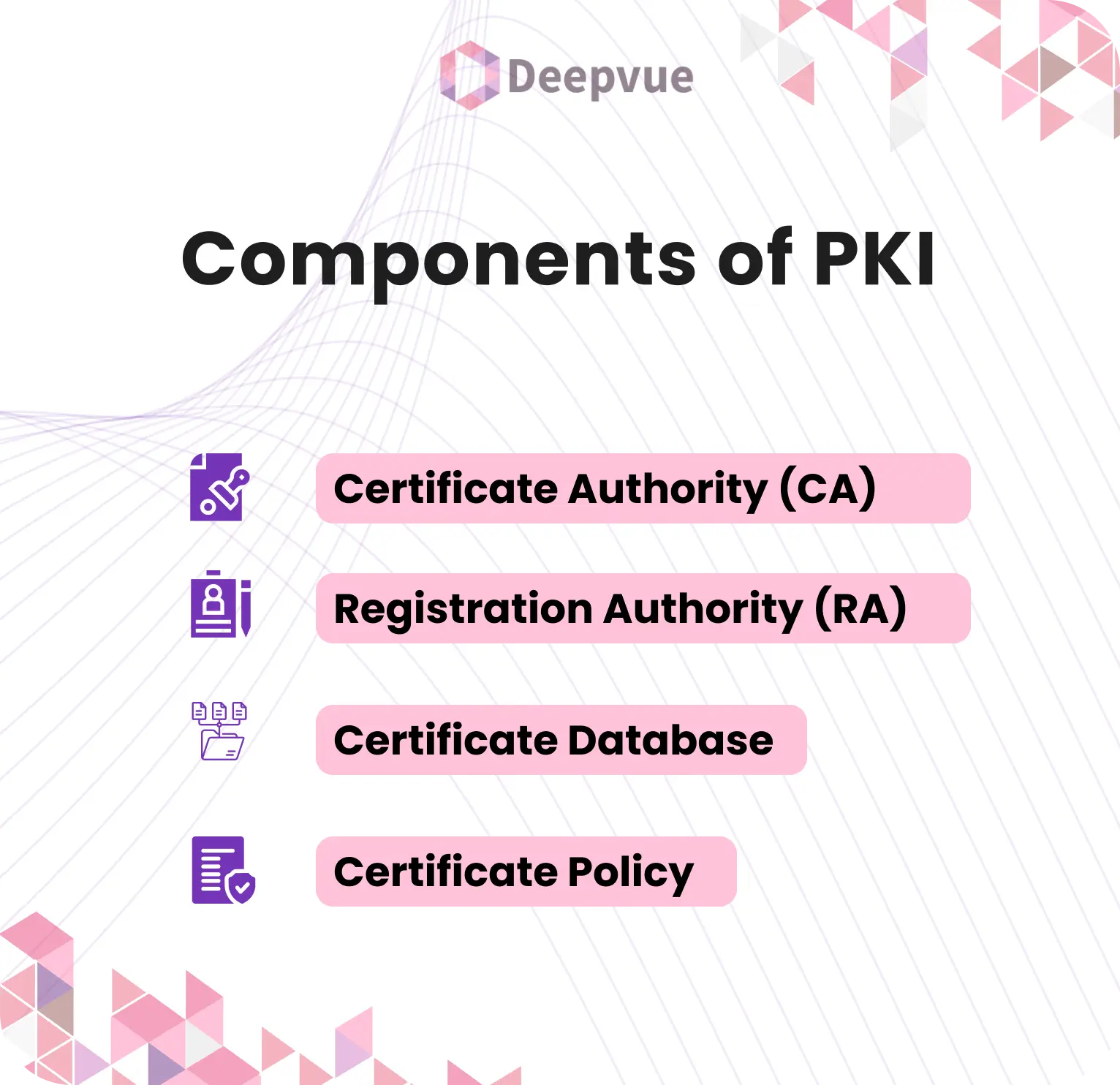
Components of PKI
Various components work together in PKI ensuring secure transactions over the internet;
- Certificate Authority (CA)– CA authenticates and issues digital certificates. It signs them using its own secret key thereby certifying that they are original.
- Registration Authority (RA)– RA plays an intermediary role between the end-user and CA. It checks who is applying for certification then passes it onto CA.
- Certificate Database– This is where all issued certificates are kept with their validity status i.e. valid, expired or revoked.
- Certificate Policy– It describes a set of rules and procedures that guide how certificates are issued and managed respectively ensuring they remain consistent without compromising security
Importance of PKI in Digital Security
Secured digital communications and transactions make PKI crucial. It ensures:
- Confidentiality– Only the verified recipient can decrypt and read the message.
- Integrity– The message was not changed during transmission.
- Authentication– Sender’s identity is confirmed.
- Non-repudiation– The sender cannot deny sending the message.
Applications of PKI
The following cases show other ways in which PKI is utilized:
- Secure Websites: Websites use PKI to secure communications between web servers and browsers. Digital certificates known as SSL/TLS certificates encrypt data sent over the internet.
- Email Security: Emails are encrypted using PKI to ensure that only the intended recipient can access them. Besides, it authenticates the sender’s identity too.
- Document Signing: Digital signatures created using PKI ensure that documents are authentic and have not been tampered with.
- Access Control: It is used to protect access to networks and systems so that only authorized users will be allowed into sensitive information areas
PKI in the Indian Market
India is experiencing a boom in online money transfer and PKI has become important in the protection of financial data and personal information. To cater to the needs of the Indian market, Deepvue.tech offers strong PKI solutions. Our PKI structure ensures that firms can securely undertake online transactions while guarding against fraud or data loss.
Implementing PKI
In order to implement PKI, there are several steps involved:
- Assessment– The security needs of your organization should be assessed.
- Planning– A comprehensive PKI strategy needs to be planned along with its policies and procedures.
- Implementation: Establish the PKI with a CA, RA, and certificate management systems.
- Training: Conduct training for all users in using and managing digital certificates.
- Monitoring: Conduct effective monitoring of the PKI system to ensure that it is effective and secure.
Conclusion
Digital communications and transactions need public key infrastructure (PKI) for their safety. At Deepvue.tech, we have implemented the best practices of the PKI framework to provide security & reliability to our users. With our expertise & customized approach, you can run your business safely & effectively in this digital era.
FAQs
What is a digital certificate in PKI?
The digital certificates used in PKIs are electronic documents issued by CAs using digital signatures to bind public keys to identities, like the name of a person or an organization. Much like a digital passport, it may be used in confirming a certificate holder’s identity and allows secure and encrypted communication.
How does PKI ensure the security of online transactions?
PKI ensures the security of online transactions since asymmetric encryption is a key pair where there is the public key used for encrypting the data, and the respective private key is used in decrypting it. This will in effect assure confidentiality of important information; at the same time, the persons’ identity is authenticated in a transaction.
What role does a Certificate Authority (CA) play in PKI?
Basically, a Certificate Authority is a person or entity trusted to issue, maintain, and revoke digital certificates. The CA checks an entity’s identity requesting that a certificate be issued and later signs it with its private key to provide trust and assurance that an entity is who he claims to be.
Can PKI be used for internal communications within an organization?
Yes, PKI can secure the internal communications of any organization because all the information passed between the employees, departments, and systems in any organization will be sensitive and would not be accessed by any unauthorized person. This shall include that emails, internal documents, and other communication conducted over the internal network will have to be encrypted.
How can businesses in India benefit from implementing PKI solutions providers?
There are a number of ways in which PKI solutions providers can benefit businesses in India.
- Scalability: Design scalable security measures that keep pace with the growing demand of your business.
- Increased Security: Ensure that all sensitive data and communications are safe from any cyber attack.
- Compliance with Regulations: Adherence to/in compliance with all required and relevant local and international data protection regulation rules.
- Trust and Credibility: Safe transactions and other communications build trust among customers and partners.
- Reduced Costs: Minimize the risk of data leakage and its associated cost.