Secure management of digital identities is now among the greatest challenges of the internet age. Legacy systems heavily depend on centralized controls, leaving individual data at risk of breaches, abuse, and theft. Decentralized identity (DID) provides a revolutionary solution, empowering individuals to own their information without relying on a single governing authority.
Based on blockchain and cryptographic technologies, decentralized identity systems offer more privacy, interoperability, and security against cyberattacks. By enabling users to control their digital credentials directly, DID systems are transforming the future of online trust and authentication.
What is Decentralized Identity?
Decentralized Identity (DID) refers to a system where individuals hold their own digital identities independently without the need for a central institution such as a government, bank, or social media platform. Rather than third-party control over personal data, users are owners, administrators, and sharers of their credentials directly through safe cryptographic processes.
Traditional Digital Identity vs. Decentralized Identity
Traditional Digital Identity is founded on centralized actors (e.g., technology companies, banks) issuing, storing, and verifying identity credentials. This invites risks such as data breach, identity fraud, and the lack of user control over personal information.
Decentralized Identity puts control back in the hands of the individual, enabling them to selectively disclose information without having to trust a central party. Personal information remains with the user and is only disclosed when absolutely necessary, improving privacy and security.
Role of Blockchain in Decentralized Identity
Blockchain technology serves as the foundation for decentralized identity in the form of a tamper-proof, open, and verifiable ledger in which identity data and credential issuance can be anchored. It supports:
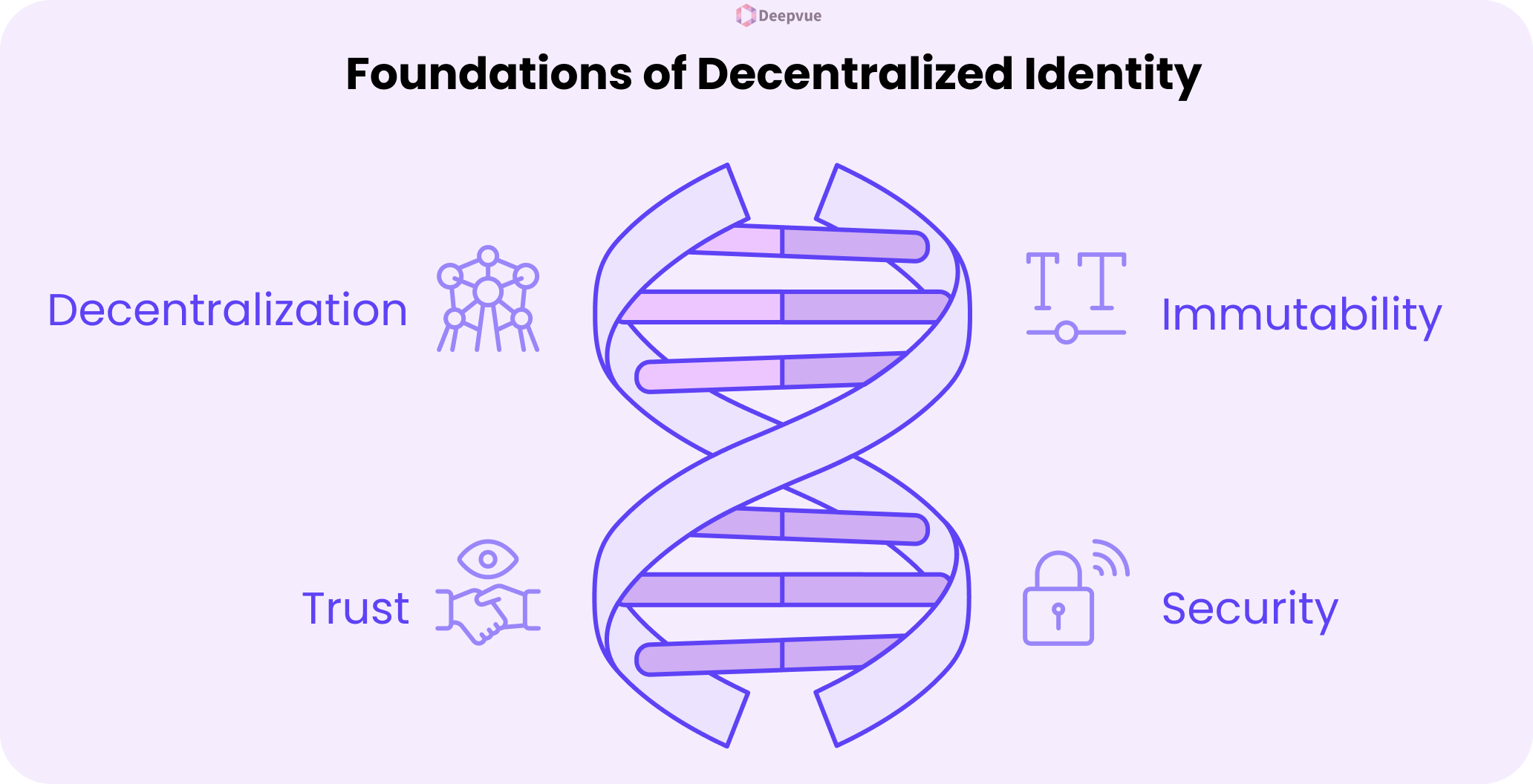
- Decentralization: One point of control for identity information.
- Immutability: Credential proofs cannot be tampered with undetectably.
- Trust: Verifiers (like governments, universities) may produce universally verifiable assertions.
- Security: Public-key cryptography guarantees that only the legitimate owners can view and exchange their identity information.
How Decentralized Identity Works?
Decentralized Identity leverages blockchain and cryptographic technologies to create self-sovereign identities that users control independently. Rather than using centralized authorities, users keep their credentials in digital wallets and present verified information to third parties using cryptographic proofs while maintaining privacy and data security.
Key Frameworks of Decentralized Identity
- Self-Sovereign Identity (SSI): Self-Sovereign Identity (SSI) is a digital identity model where individuals fully own, control, and manage their personal data without relying on a central authority. Users can choose to share authenticated information with other people while maintaining control over who receives their identity information.
- Decentralized Identifiers (DIDs): Decentralized Identifiers (DIDs) represent a new category of digital identifiers that are developed, controlled, and owned by the user outside of any centralized authority. DIDs reside on distributed ledger technologies (such as blockchains) and are employed to create secure, verifiable digital identities.
Benefits of Decentralized Identity
- Improved Privacy and Security: Decentralized identity makes data breaches at a central point more difficult, as personal data is not held in one weak database but is stored across secure, distributed systems. Users only provide the bare essentials of data, limiting exposure to harm.
- User Control Over Personal Data: With a decentralized digital identity, users are in complete control of who has access to their personal details. They can authorize, restrict, or withdraw permissions whenever they want, making sure that their information is utilized only with their consent.
- Interoperability and Seamless Authentication: Decentralized identity systems are compatible with many platforms and services and enable users to authenticate themselves rapidly and securely without requiring multiple passwords or opening new accounts for each service.
Challenges in Adopting Decentralized Identity
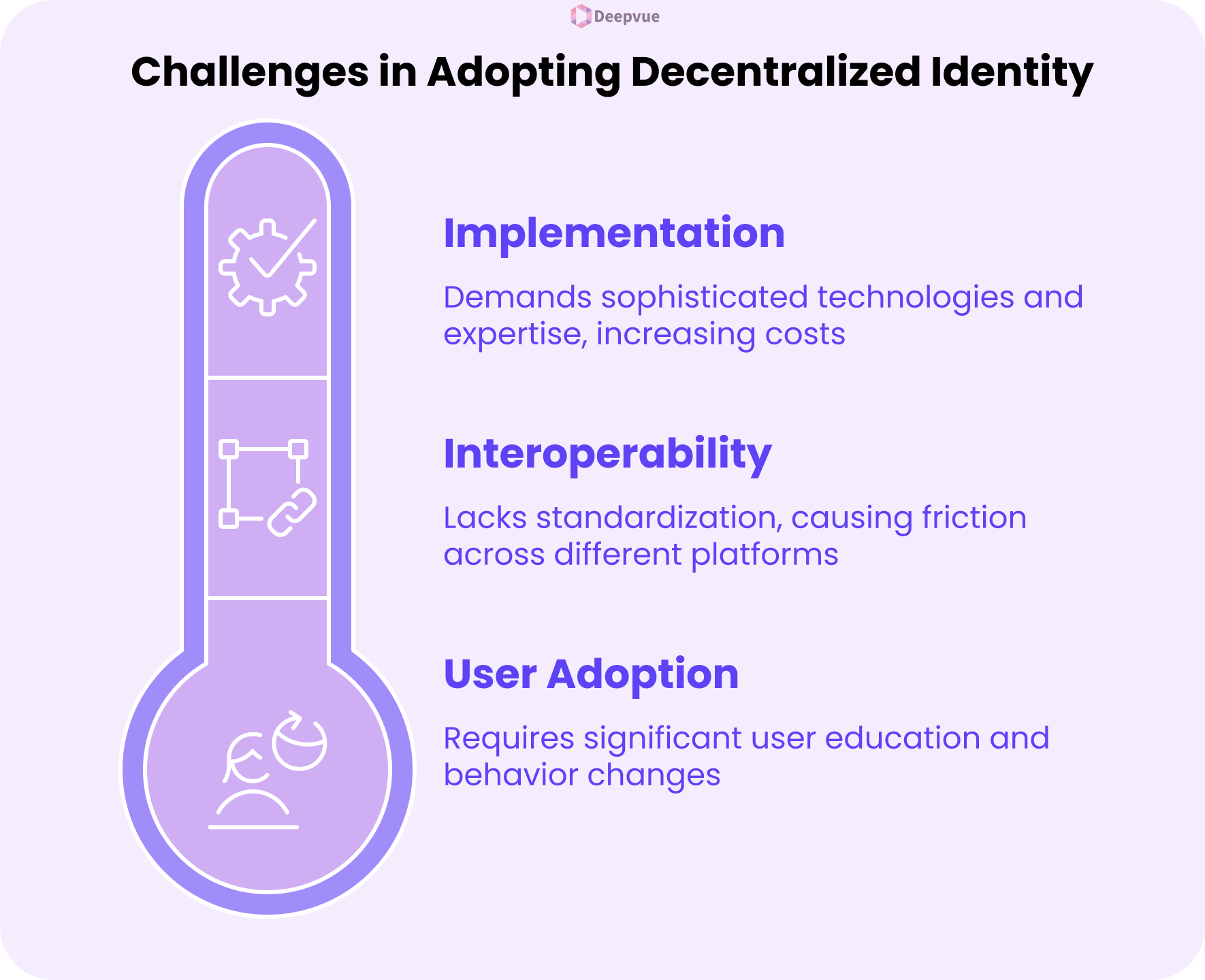
- User Behavior Adaptation: People are used to centralized systems and can be puzzled and unable to trust decentralized identity models. Getting users to learn how to safely handle their own credentials is one of the big challenges, and the risk of losing access due to improper management (such as losing private keys) can make people resistant.
- Interoperability Problems: Decentralized identity products tend to lack standardization, and it is difficult for various platforms, apps, and systems to communicate seamlessly with each other. In the absence of shared frameworks and protocols, users and service providers experience friction when attempting to adopt or use decentralized identities in multiple services.
- Complexity of Implementation: Implementing decentralized digital identity systems requires sophisticated technologies such as blockchain, cryptographic proofs, and decentralized identifiers (DIDs). Companies have to spend money on new infrastructure, expertise, and security protections, which raises the cost of development and delays adoption.
Technology and Infrastructure
Blockchain Technology
Blockchain technology is a decentralized digital ledger that records transactions securely and transparently across a distributed network. It increases trust, minimizes the risk of fraud, and enhances the efficiency of processes such as payments, supply chain tracking, and identity verification.
Cloud Computing Innovations
Cloud computing technology has transformed the way companies store, process, and retrieve information. Technologies such as multi-cloud strategies, edge computing, AI integration, and improved cybersecurity have improved the speed, flexibility, and security of cloud services, allowing for greater scalability and cost-effectiveness.
Case Studies and Examples
- Microsoft’s ION Network: A public, open-source layer based on Bitcoin that enables decentralized identifiers for organizations and users.
- IDunion (Germany): A European consortium that is constructing a decentralized identity ecosystem to be used throughout the public and private sectors.
- Sovrin Network: An open-source, decentralized digital identity network dedicated to privacy-respecting credential exchanges.
- India’s Aadhaar Evolution: Although Aadhaar began as centralized, India is investigating decentralized layers to enhance user privacy in digital identity authentication
Conclusion
Decentralized identity represents a revolutionary departure from legacy models, minimizing dependence on centralized databases and giving individuals control over their own credentials. For businesses, the adoption of decentralized models not only provides security but also promotes deeper trust with customers.
At Deepvue.tech, we bridge the divide between innovation and security through advanced identity verification technologies that can interoperate with decentralized identity patterns. Our identity verification API gives frictionless, compliant, and safe verifications to empower organizations to secure user information while improving user experience.
FAQ
What is decentralized identity (DID)?
Decentralized identity is a digital identity model where individuals control their own credentials without relying on centralized authorities, typically using blockchain technology.
How does decentralized identity work?
It uses distributed ledgers and cryptographic proofs, allowing users to store and manage credentials securely in personal digital wallets.
Why is decentralized identity important?
It enhances privacy, reduces the risk of large-scale data breaches, and gives individuals ownership of their personal data.
What technologies power decentralized identity?
Blockchain, decentralized identifiers (DIDs), verifiable credentials, and cryptographic techniques are key enablers of decentralized identity.
Who benefits most from decentralized identity?
Everyone benefits—from individuals seeking privacy to businesses aiming for stronger customer trust and regulatory compliance.