Identity theft is a familiar financial crime, but synthetic identity theft is less well understood but growing in prevalence. Instead of stealing a complete identity, crooks mix real and fake information to create a new, fake identity. Synthetic identity fraud is on the rise, with personal information becoming more susceptible to exploitation. Being aware of the dynamics of this form of fraud is crucial for both individuals and financial institutions. This article explores the dynamics of synthetic identity theft, how it operates, and the distinction from classical identity theft. By bringing these issues to light, we can more effectively fight the spread of synthetic identity fraud and guard our identities.
What is Synthetic Identity Fraud?
Synthetic identity fraud is a form of identity theft that involves the creation of a fake identity by combining real and fabricated personal information. In contrast to traditional identity theft, where a scammer appropriates an existing person’s identity, synthetic identity theft synthesizes an identity that might not even be present anywhere in official documents. The sophisticated nature of such fraud makes it widely utilized to get credit cards, loans, and other financial products without anyone realizing it. The consequences for the victims of synthetic identity fraud can be devastating, with ruined credit ratings and financial uncertainty being just some of the outcomes.
How Synthetic Identity Fraud Works?
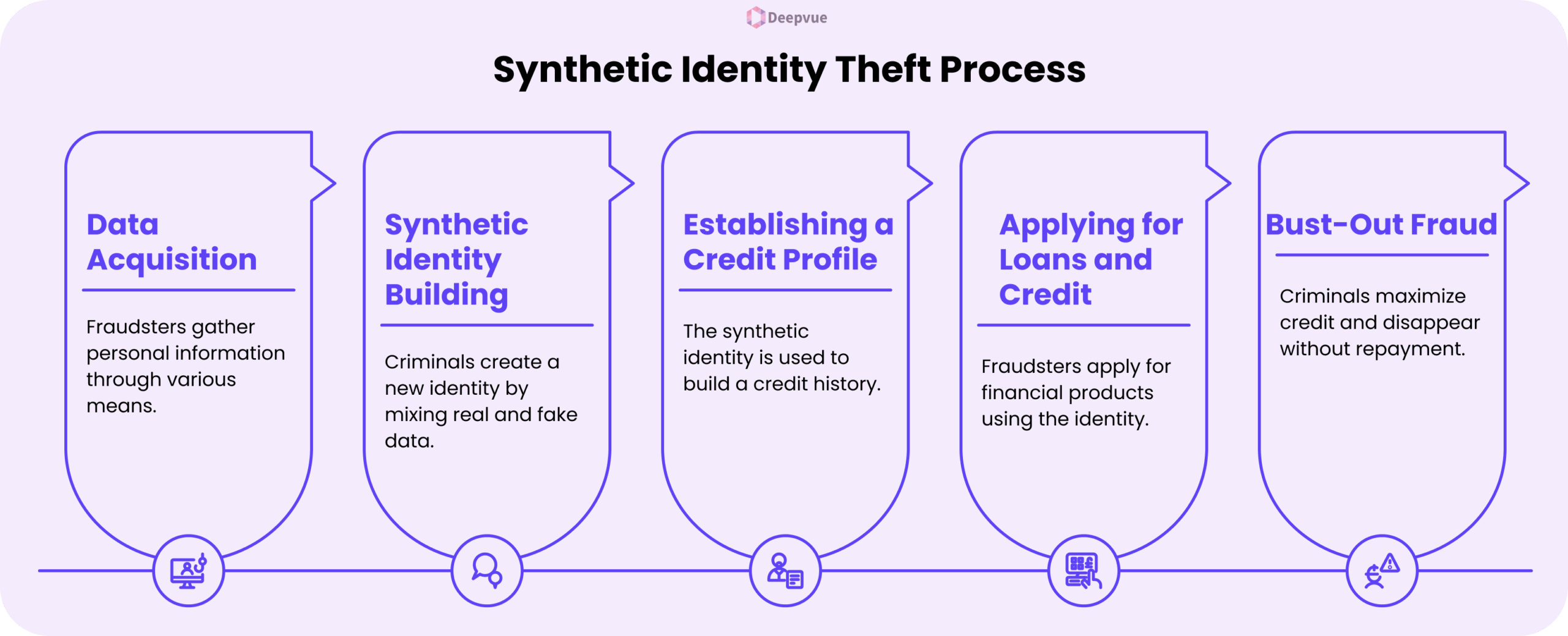
Step 1: Data Acquisition
Fraudsters obtain personal information through data breaches, phishing, or purchasing data on the dark web. The information obtained can be SSNs, names, and any other personally identifiable information (PII).
Step 2: Synthetic Identity Building
Once the required information is gathered, criminals mix actual information with phony data to create a new identity. This can include the use of a valid SSN but linking it to a false name and address.
Step 3: Establishing a Credit Profile
The artificial identity is then utilized to obtain credit. In the beginning, applications will be denied, but the idea is to build a presence in the credit system. The criminals can utilize methods such as piggybacking, whereby they are added as authorized users on good accounts to establish credit.
Step 4: Applying for Loans and Credit
After the synthetic identity acquires a credit record, fraudsters can obtain loans, credit cards, and other credit products. They can have a good payment record in the early stages to raise credit limits.
Step 5: Bust-Out Fraud
Once credibility is established and significant credit is obtained, the fraudsters perform a “bust-out,” maximizing available credit and vanishing without repayment. This is generally the ultimate phase of synthetic identity fraud, leaving financial institutions and lenders to absorb the losses.
Comparison with Traditional Identity Theft
Traditional identity theft exploits the unauthorized use of an existing person’s identity, synthetic identity fraud has a different problem. Old-fashioned identity thieves tend to steal data about individuals to impersonate an existing person, but synthetic identity thieves construct an artificial identity that is not necessarily linked to a real person. This makes it more complicated for banks and other financial institutions to detect fraudulent activity because the synthetic identities look genuine. Knowledge of the differences between these two types of identity fraud is important to formulate measures on how to address risks and augment identity protection.
The Mechanics of Synthetic Identity Theft
Synthetic identity is a willful act that entails the construction of actual and false personal data in a specific and meticulous manner. Scammers can utilize an original Social Security Number, either of a child or a deceased person, and pair it with an alias date of birth and some other made-up information to form a synthetic identity. The new identity can be carried through initial identity verification procedures unscathed, making it possible for criminals to open accounts and commit financial fraud without immediate detection. The construction of synthetic identities, therefore, illustrates the weaknesses that exist in existing systems of identity verification.
Common Techniques Used by Fraudsters
- Applying Children’s SSNs: Child identities are the more desirable targets since they are less likely to have pre-existing credit histories. These SSNs can be manipulated by fraudsters for years until the crime is revealed.
- Credit Piggybacking: Linking a synthetic identity to an existing, good credit account to establish credit history. This method utilizes a proven credit history from an actual account to add credibility to a synthetic profile.
- Address Manipulation: Scammers can utilize drop addresses or empty buildings to accept false statements and evade detection. Scammers may also employ virtual addresses or P.O. boxes to conceal their real location.
- Account Tumbling: Creating numerous accounts to cover up fraudulent transactions and make it difficult for monitoring systems to detect them. This method may include creating several accounts across various financial institutions to spread the fraudulent transactions and prevent red flags.
Impact of Synthetic Identity Theft
Synthetic identity theft is expensive for banks, with losses amounting to millions of dollars. In traditional identity theft, the crime is usually reported by a real victim. Synthetic identities usually take a long time to be detected. The consequences include:
- Economic losses for creditors and lenders. Synthetic identities are able to obtain various loans and credit cards, which end up as uncollectible debt when the fraud artist disappears.
- Reputational harm to impacted financial institutions. Failure to identify synthetic identities threatens customer trust.
- Debt collection challenges because there is no real person behind the fake profile. Creditors might find it difficult to track down the criminal since the synthetic identity does not exist in the real world.
- Long-term damage to credit for individuals whose SSN was used without consent. This can impact children whose SSNs were used, possibly to their detriment in the future when they try to get legitimate credit.
Detecting and Preventing Synthetic Identity Theft
- Strong Identity Verification: Enforce multi-layered verification checks to authenticate identities during onboarding.
- Data Analytics and Artificial Intelligence: Leverage machine learning to identify patterns pointing toward synthetic identities, for example, discrepancies in information or abnormally fast credit establishment.
- Coordination with Credit Bureaus: Track credit reports for irregularities, such as the opening of a new profile with minimal history.
Related Read: How Aadhaar Masking Protects Customer Data and Prevents Identity Theft?
Conclusion
Synthetic identity theft poses a special problem because it mixes actual and false information to construct seemingly valid identities. For financial institutions, the solution to reducing this risk is strong identity verification, anomaly monitoring, and consumer education on the risks of synthetic identities. Enhancing defenses against synthetic identity theft is critical in protecting financial ecosystems from this emerging threat.
Our identity verification API is an effective weapon against synthetic identity fraud. Utilizing sophisticated algorithms, real-time checks on data, and multi-level verification processes, our solution assists financial institutions in spotting suspicious profiles, authenticating user identities, and blocking fraudulent transactions before they reach advanced stages.
FAQ
What is synthetic identity theft?
Synthetic identity theft is the process of constructing a false identity by combining real and fictional information, like an authentic SSN with a false name and address.
How does synthetic identity theft differ from traditional identity theft?
Traditional identity theft is stealing and utilizing an existing person’s identity, whereas synthetic identity theft constructs a whole new identity that doesn’t necessarily connect to an individual.
Why are children’s SSNs appealing to fraudsters?
Children’s SSNs tend to be inactive, so it is easier for fraudsters to establish a credit profile on a synthetic identity without the fraudulent activity being detected right away.
How do fraudsters establish a credit profile on synthetic identities?
They begin by applying for credit under the synthetic identity. Although they might be denied the credit initially, the application creates a record. Eventually, they use methods such as piggybacking to accumulate credit history.
What is bust-out fraud in synthetic identity theft?
Bust-out fraud involves a fraudster exhausting the credit of a synthetic identity and then vanishing, leaving lenders with uncollectible debt.








