Verifying an individual’s identity has become a critical part of maintaining security and trust. This process, known as identity proofing, is essential for preventing fraud and ensuring that only legitimate users gain access to sensitive systems and services.
But what exactly is identity proofing, and why is it so important? In this article, we’ll explore the concept of identity proofing, its importance, and how it’s implemented, especially in the context of financial services and integrations offered by Deepvue.
What is Identity Proofing?
Identity proofing is the process of verifying that an individual is who they claim to be. This involves validating the authenticity of the information provided by the user and confirming that it matches an actual, verified identity. The goal is to ensure that the individual’s claimed identity corresponds to their real-world identity.
Claimed Identity vs. Actual Identity
- Claimed Identity: This is the information provided by the user, which is initially unverified. It includes details such as name, address, and date of birth that the user asserts are theirs.
- Actual Identity: This is the verified and validated information that proves the user is who they say they are. This involves cross-checking the claimed identity with trusted sources or documents.
Why is Identity Proofing Important?
Identity proofing plays a crucial role in safeguarding personal and sensitive information. Here are some key reasons why it’s important:
1. Preventing Fraud and Identity Theft
Identity proofing helps prevent fraud by ensuring that only verified individuals can access sensitive information or services. It reduces the risk of identity theft, where malicious actors use someone else’s identity to commit crimes or fraud.
2. Compliance with Regulations
Many industries, particularly financial services, are subject to regulations that require robust identity verification processes. For instance, anti-money laundering (AML) regulations and know your customer (KYC) requirements mandate financial institutions to verify the identities of their clients to prevent illegal activities.
3. Enhancing Security
By verifying identities, organizations can enhance their overall security posture. It ensures that access to systems and data is restricted to legitimate users, reducing the risk of unauthorized access and data breaches.
4. Building Customer Trust
Customers are more likely to trust organizations that take their security seriously. Effective identity proofing helps build trust by demonstrating that the organization is committed to protecting their personal information.
How Identity Proofing Works
Identity proofing is a step-by-step process to ensure that an individual is who they claim to be. Here’s how identity proofing typically works:
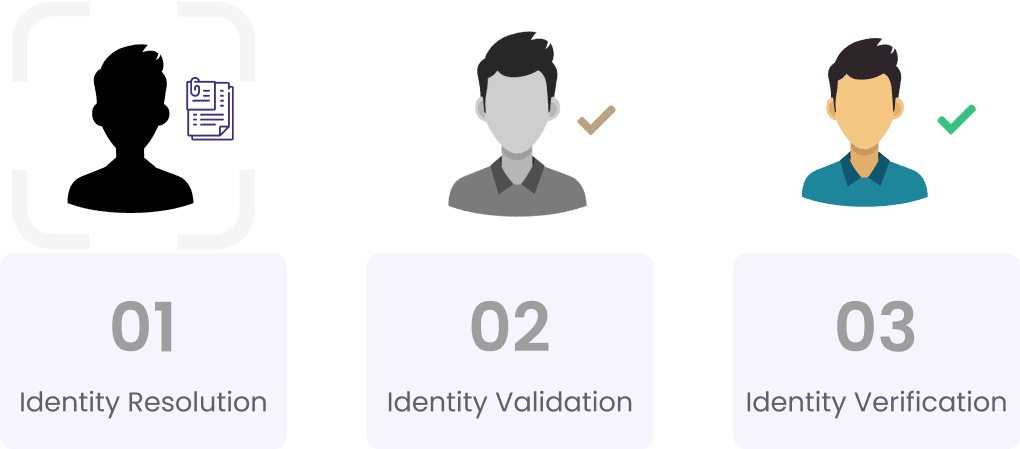
1. Identity Resolution
The first step in identity proofing is identity resolution, which involves identifying an individual within a given population or system. This is done using basic information such as name, date of birth, and address, and ensuring that these details are unique enough to differentiate the person from others.
2. Identity Validation
Once the individual has been identified, the next step is to validate the provided information. This involves collecting proof of identity, such as government-issued documents (e.g., passport, driver’s license) or biometric data (e.g., fingerprints, facial recognition). This information is then checked for accuracy and authenticity.
3. Identity Verification
The final step is identity verification, where the validated information is cross-referenced with trusted sources to confirm that the individual is who they claim to be.
Methods of Identity Proofing
Identity proofing can be conducted using various methods, depending on the level of assurance required. Here are some common methods:
1. Biometric Verification
Biometric verification uses unique physical characteristics, such as fingerprints, facial recognition, or iris scans, to verify an individual’s identity. This method is highly reliable and difficult to fake.
2. Knowledge-Based Verification
This involves asking the user to provide information that only they would know, such as answers to security questions or details about their personal history. While useful, this method can be less secure if the information is easily accessible or guessable.
3. Document Verification
This method involves verifying identity documents such as passports, driver’s licenses, or national ID cards. The documents are checked for authenticity and validity to confirm the user’s identity.
4. Out-of-Band Verification
Out-of-band verification requires the user to verify their identity through a separate communication channel, such as receiving a code via SMS or email. This adds an extra layer of security by ensuring the individual has access to multiple forms of contact.
Implementing Effective Identity Proofing
Implementing effective identity proofing requires a balanced approach that ensures security without compromising user experience. Here are some key steps:
1. Determine the Level of Assurance Required
Different situations require different levels of identity proofing. For example, signing up for a newsletter might not require any identity proofing, while opening a bank account would require a high level of assurance.
2. Select Appropriate Methods
Choose identity proofing methods that match the required level of assurance. For high-risk scenarios, biometric verification or in-person document verification might be necessary, while lower-risk situations might only require knowledge-based verification.
3. Ensure User-Friendly Processes
The identity proofing process should be seamless and user-friendly. Complicated or cumbersome processes can frustrate users and lead to abandonment. Aim for a balance between security and convenience.
4. Integrate with Existing Systems
Identity proofing should integrate smoothly with existing systems and workflows. This ensures that the process is not only secure but also efficient and scalable.
Identity Proofing in Financial Services
In the financial sector, identity proofing is especially critical. Financial institutions must comply with stringent regulations to prevent money laundering and fraud. Here’s how identity proofing is typically used:
1. Account Opening
When a customer opens a bank account, the financial institution must verify their identity to comply with KYC regulations. This often involves document verification and, in some cases, biometric checks.
2. Online Transactions
For online transactions, identity proofing helps ensure that the person making the transaction is authorized to do so. This can involve out-of-band verification or biometric authentication.
3. Compliance and Reporting
Financial institutions must maintain records of identity verification processes to demonstrate compliance with AML and KYC regulations. This involves securely storing the verified information and ensuring it can be audited.
Conclusion
Identity proofing is a fundamental aspect of maintaining security and trust in a digital world. By verifying that individuals are who they claim to be, organizations can prevent fraud, comply with regulations, enhance security, and build customer trust.
Effective identity proofing is not just a regulatory requirement but a crucial part of delivering secure and reliable services. By implementing robust and user-friendly identity proofing methods, organizations can ensure that they are well-protected against identity-related threats.
To learn more about how Deepvue’s Verification Suite can enhance your verification process, visit Deepvue.tech and explore our range of APIs designed to ensure accuracy and efficiency.
FAQs
What is identity proofing?
Identity proofing is the process of verifying that an individual is who they claim to be. It involves validating the authenticity of the information provided by the user and confirming that it matches an actual, verified identity. This ensures that the person accessing services or data is legitimate.
Why is identity proofing important for financial institutions?
Identity proofing is crucial for financial institutions to prevent fraud, comply with regulations such as anti-money laundering (AML) and know your customer (KYC) requirements, enhance security, and build customer trust. It ensures that only verified individuals can access financial services and sensitive information.
What are common methods of identity proofing?
Common methods of identity proofing include:
Out-of-Band Verification: Using separate communication channels, like SMS or email, for verification.
Biometric Verification: Using fingerprints, facial recognition, or iris scans.
Knowledge-Based Verification: Asking security questions or personal history details.
Document Verification: Verifying identity documents such as passports or driver’s licenses.
How does biometric verification work in identity proofing?
Biometric verification involves using unique physical characteristics, such as fingerprints, facial recognition, or iris scans, to verify an individual’s identity. This method is highly reliable and difficult to fake, providing a strong layer of security.
What should organizations consider when implementing identity proofing?
When implementing identity proofing, organizations should:
Integrate with Existing Systems: Ensure seamless integration with existing workflows and systems for efficiency and scalability.
Determine the Level of Assurance Required: Different scenarios require different levels of identity proofing.
Select Appropriate Methods: Choose methods that match the required assurance level.
Ensure User-Friendly Processes: Balance security with user convenience to avoid frustrating users.