Protection of sensitive information is a prime concern for businesses of all scales. Cyber attacks, data breaches, and compliance with regulations render it necessary for companies to ensure strong security mechanisms. This is where ISO 27001, the globally acclaimed standard for managing information security, steps in.
But what is ISO 27001, and why is it important? In this blog, we’ll break down the key components of the standard, explore its benefits, and explain how organizations can achieve compliance.
What is ISO 27001?
ISO 27001 provides a systematic approach to managing and protecting sensitive information, ensuring confidentiality, integrity, and availability. It outlines best practices for developing an Information Security Management System (ISMS), assisting organizations in identifying risks, deploying security controls, and improving their cybersecurity stance continuously. Obtaining ISO 27001 certification indicates that a company is serious about data protection, and establishing trust among customers, partners, and stakeholders.
Importance of ISO 27001
ISO 27001 is crucial for organizations because it offers a systematic framework to safeguard sensitive information, mitigate risks, and maintain compliance with legal and regulatory standards. ISO 27001 implementation ensures that companies protect themselves from cyber attacks, data breaches, and unauthorized access by putting in place strong security controls and ongoing monitoring processes. It also promotes customer, partner, and stakeholder confidence by proving a commitment to data protection and risk management.
Additionally, ISO 27001 improves operational efficiency by identifying vulnerabilities and implementing proactive security measures. Compliance with this standard can also provide a competitive advantage, as many clients and regulatory bodies require organizations to adhere to stringent security protocols.
Benefits of Implementing ISO 27001
- Enhanced Risk Management: Assists in identifying, analyzing, and reducing security threats to lower the possibility of data leaks and cyber-attacks.
- Legal Compliance: Guarantees compliance with data protection legislation and regulatory standards, preventing fines and legal problems.
- Increased Credibility with Clients: Establishes customer trust by proving dedication to data protection and information security.
Steps to achieve ISO 27001 certification
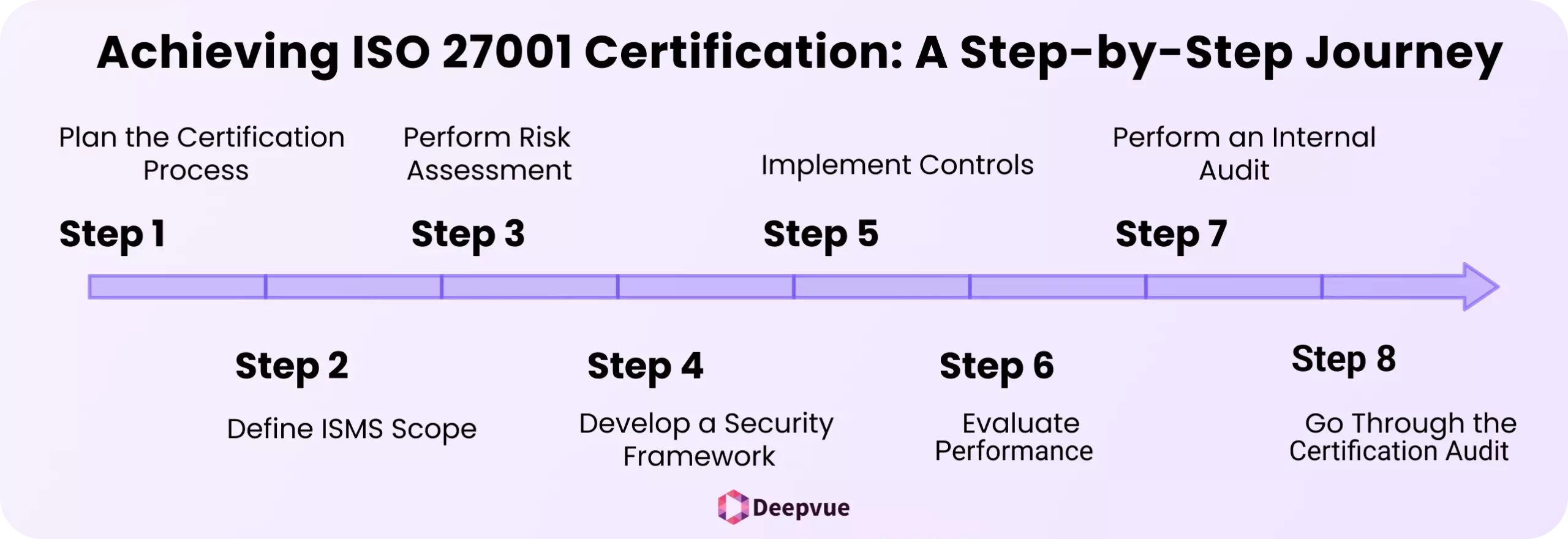
Step 1: Plan the Certification Process
Understand ISO 27001 requirements and secure leadership support to drive implementation.
Step 2: Define ISMS Scope
Clearly outline the systems, processes, and people included in your ISMS to focus efforts and reduce certification costs.
Step 3: Perform Risk Assessment
Examine your security posture and determine and rank risks that must be remediated.
Step 4: Develop a Security Framework
Utilize risk assessment results to develop a framework of controls, policies, and procedures for implementation and audit readiness.
Step 5: Implement Controls
Begin deploying controls, define responsibilities, and prioritize activity based on the severity of the risk.
Step 6: Evaluate Performance
Periodically check performance data to identify recurring weaknesses and correct them before the final audit.
Step 7: Perform an Internal Audit
Audit your ISMS internally to identify gaps, confirm effectiveness, and improve before the certification audit.
Step 8: Go Through the Certification Audit
A certified auditor performs a two-stage audit:
- Stage 1: Examines documentation, risk reports, and plans for implementation.
- Stage 2: Ensures real-world implementation and effectiveness of your ISMS.
If nothing significant is uncovered, certification is issued.
Step 9: Maintain & Improve
Regularly maintain and enhance your ISMS to achieve security targets and maintain certification.
The Annex A Controls
ISO 27001 Annex A is a collection of suggested security controls intended to mitigate information security threats. It is not a checklist to be ticked but a guideline—organizations select applicable controls based on their risk assessment and risk treatment plan. Annex A controls are intended to safeguard data confidentiality, integrity, and availability. They are best practices and the bare minimum an organization should take into account depending on its scope and risk.
Whereas the Infosec Officer or team handles the implementation and compliance, all workers have a contributing role to play, being the first line of defense. There must be the involvement of the management since policy and procedure demand their review and approval at all major stages. Hence, introducing Annex A is a collective task.
Risk Management Methodology in ISO 27001
ISO 27001 applies a structured risk management methodology to determine, assess, and address information security risks. It starts with the establishment of the risk assessment criteria, such as risk acceptance levels and impact likelihood scales. The organization needs to specify information assets and determine threats, vulnerabilities, and potential impacts. Risks are analyzed and assessed to decide on their significance according to established criteria.
Based on this evaluation, the organization selects appropriate risk treatment options, such as reducing, avoiding, sharing, or accepting the risk. A treatment plan for risks is created to record actions, roles, and deadlines. Controls to be selected are to come from Annex A (or another source) to treat the identified risks. Residual risk has to be approved by management, ascertaining it is within tolerable limits. The process ensures improvement of the Information Security Management System (ISMS) continually.
Differences between ISO 27001 and other standards
ISO 27001 vs ISO 9001
- ISO 27001 focuses on information security management. ISO 27001 protects confidentiality, integrity, and availability of information.
- ISO 9001 focuses on quality management systems and ensuring consistent product/service quality. ISO 9001 improves customer satisfaction and process efficiency.
ISO 27001 vs NIST Cybersecurity Framework
- ISO 27001 is a certifiable standard for establishing an Information Security Management System (ISMS). ISO 27001 is an international standard developed by ISO/IEC.
- NIST CSF is a voluntary framework providing guidelines to manage cybersecurity risks. NIST CSF is developed by the U.S. National Institute of Standards and Technology.
SOC 2 vs ISO 27001
- SOC 2 evaluates how well a company manages customer data based on five trust principles (security, availability, processing integrity, confidentiality, and privacy).
- ISO 27001 provides a comprehensive framework for establishing, implementing, and maintaining an Information Security Management System (ISMS).
Advantages for Small and Medium Enterprises
ISO 27001 is particularly useful to small and medium-sized businesses (SMEs) as it provides a structured method of managing information security. ISO 27001 helps SMEs build increased customer and business partner confidence by demonstrating their commitment to the protection of confidential data. ISO 27001 helps organizations identify potential areas of security weaknesses and implement controls to reduce them, leading to better handling of risk and a more robust organization.
Further, ISO 27001 ensures conformity with a host of legal and regulatory requirements such as GDPR and HIPAA, reducing the chance of legal penalties. It also boosts the reputation and competitiveness of the company, usually being a condition for winning contracts with big clients or entering new markets. Overall, it provides SMEs with a great competitive advantage while setting the ground for sustainable growth and long-term success.
Related Read: MSME Verification: How Businesses Can Verify MSMEs in India
Conclusion
ISO 27001 is more than a certification—it’s a forward-looking management approach to keeping information security risk in check on a structured, dependable basis. Organizations that embrace its principles, not only better secure their data but also build a competitive advantage, enhance customer trust, and satisfy regulatory conditions.
If you’re prepared to take that next step towards protecting your organization’s data, contact us here — we’re here to assist you through the ISO 27001 process with confidence.
Questions
What is the ISO 27001 standard for information security?
ISO 27001 is an international standard that outlines best practices for establishing, implementing, and maintaining an Information Security Management System (ISMS).
What are the 3 main components of information security in ISO 27001?
The three fundamental components include confidentiality, integrity, and data availability.
What are the 4 areas of ISO 27001?
The four major categories are organizational, people, physical, and technological security controls.
What are the principles of information security in ISO 27001?
The key principles are risk management, ongoing improvement, and safeguarding information assets using organized policies and controls.








